Announcing Secure DNS with Twingate
Alex Marshall
•
•
Aug 2, 2022

Businesses around the world are in the midst of a tectonic shift to support a work-from-anywhere workforce without sacrificing company security. Our customers tell us their IT and security teams are grappling with how to provide employees with the same ease of use they experienced when working inside a heavily protected office network. Achieving a balance of security and usability when employees are accessing both public and private resources from hundreds of individual networks all over the world is a major challenge.
A critical component of a modern security strategy is protecting internet traffic. We’re excited to announce Twingate’s very first capability to protect and encrypt not just users’ private traffic, but also the most common unencrypted traffic that flows over networks today: DNS.
The history of the Domain Name System
The Domain Name System was established in 1983 and traces its roots back to the proto-Internet, ARPANET. DNS is the global name translation system for the internet that converts human-readable network addresses such as www.google.com into machine-readable IP addresses such as “172.253.124.147‚ or “2607:f8b0:4004:c06::67‚ that networks use to route traffic from source to destination.
The DNS system converts human-readable addresses into network addresses through a distributed, hierarchical system.
Although there have been some security improvements recently, such as DNSSEC, the vast majority of DNS requests are still unencrypted and hence vulnerable to a range of exploits from data collection to perpetrating phishing attacks.
DNS-over-HTTPS (DoH) encapsulates standard DNS requests into encrypted HTTPS requests, hiding the contents of the requests from third parties. DoH requests are sent to a trusted DoH resolver endpoint, and DNS resolution is sent back to the client via the same encrypted channel. A significant benefit of DoH is its simplicity. DoH is applied without requiring any changes to the originating client application. DoH works on any network that allows Internet traffic and does not require any special configuration.
The importance of encrypting DNS traffic
The DNS system was designed with scalability in mind from the beginning through a hierarchical architecture that relies on caching name lookups at different levels of the system. This distributed system has the benefit of affording a global level of scalability, but because the system exchanges information unencrypted, this also leaves it open to attack. The ease of readability allows for eavesdropping and manipulation of the contents of these questions, making DNS a prime target for attackers.
In addition to its plaintext nature, the caching inherent to the DNS hierarchy also leaves it vulnerable to a specific type of attack known as DNS poisoning. With just the right timing—made possible by watching the unencrypted exchange of requests—an attacker can respond with a network address that they control when a user looks up a legitimate domain name. The attacker can then fake a legitimate site, collecting private information without the user’s knowledge until it’s too late.
Caption: Bad actors may spoof network addresses for legitimate names in the DNS system through an attack known as DNS poisoning.
To protect against this and many other types of DNS-based attacks, DNS queries can instead be sent through HTTPS rather than over plaintext, unvalidated UDP. This is the role that DNS over HTTPS (DoH) plays by encrypting DNS queries through encapsulation in an HTTPS request and sending them to a trusted DoH resolver. Hiding DNS queries from view is like taking a postcard, inserting it inside an envelope, and sealing it shut. DNS traffic is also hidden among other HTTPS traffic to websites and web apps, so packets can’t be as easily identified.
DNS-over-HTTPS (DoH) hides DNS traffic from view, preventing most types of DNS-based attacks.
Introducing device-wide DNS encryption with Twingate
Most modern browsers offer automatic DoH protection to trusted DoH resolvers, but DNS requests on devices are not isolated to browsers. This leaves a gap in DNS protection that Twingate is uniquely positioned to fill. The Twingate client provides configuration-less private DNS resolution, making it possible to offer automatic DoH protection for all DNS traffic on a device (for details, see how DNS works with Twingate). Not only browser-originated DNS requests are automatically encrypted—any DNS request on a user’s device, regardless of the application, gets encrypted.
The benefits of encrypting DNS traffic by default are clear, and rather than relying on application-specific configurations for DoH, such as browser-based DoH, Twingate now provides blanket DNS encryption for all DNS traffic on a device.
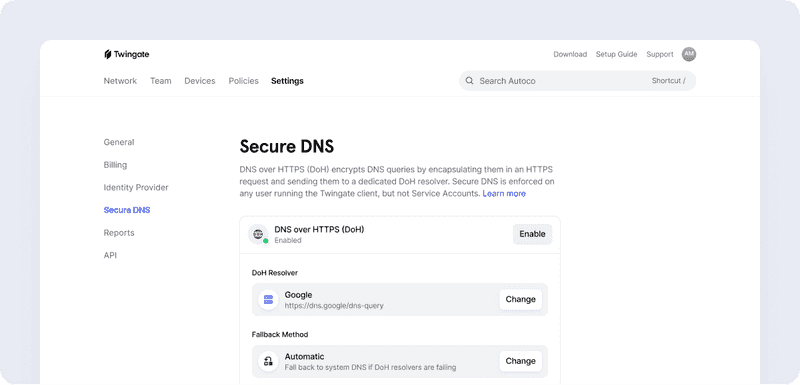
Secure DNS is enforced on any user running the Twingate Client. Twingate admins can select the DoH resolver of their choice, such as Cloudflare, Google, OpenDNS, or custom. DoH policy can be set where all DNS traffic must be encrypted for always-on protection, or as an automatic failover mode where Twingate uses regular DNS if we can’t contact the DoH resolver.
DoH applied universally across all systems and resources enforces a comprehensive defense-in-depth strategy for today’s cybersecurity threats. This system-wide DoH capability opens up new possibilities for DNS security by using the Twingate client to route DNS requests to common DNS security tools like NextDNS, Cloudflare Gateway, and others. There’s no need to install a separate, dedicated DNS security agent on the device.
This means a single Twingate client can be configured to provide private access to resources as well as secure public internet traffic, so you can leverage existing DNS filtering products to:
Apply DNS-level threat filtering against known malware and phishing sites often initiated by unsuspecting employees
Block employee access to undesirable or inappropriate content
Provide visibility into the applications employees are using to uncover potential shadow IT
Improve employee experience by blocking ads and trackers on websites
Ensure home ISPs or public wifis can’t view visited sites
Read more about this new functionality in our docs and watch a short demo of Twingate Secure DNS in action on YouTube.
Try it for free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Announcing Secure DNS with Twingate
Alex Marshall
•
•
Aug 2, 2022

Businesses around the world are in the midst of a tectonic shift to support a work-from-anywhere workforce without sacrificing company security. Our customers tell us their IT and security teams are grappling with how to provide employees with the same ease of use they experienced when working inside a heavily protected office network. Achieving a balance of security and usability when employees are accessing both public and private resources from hundreds of individual networks all over the world is a major challenge.
A critical component of a modern security strategy is protecting internet traffic. We’re excited to announce Twingate’s very first capability to protect and encrypt not just users’ private traffic, but also the most common unencrypted traffic that flows over networks today: DNS.
The history of the Domain Name System
The Domain Name System was established in 1983 and traces its roots back to the proto-Internet, ARPANET. DNS is the global name translation system for the internet that converts human-readable network addresses such as www.google.com into machine-readable IP addresses such as “172.253.124.147‚ or “2607:f8b0:4004:c06::67‚ that networks use to route traffic from source to destination.
The DNS system converts human-readable addresses into network addresses through a distributed, hierarchical system.
Although there have been some security improvements recently, such as DNSSEC, the vast majority of DNS requests are still unencrypted and hence vulnerable to a range of exploits from data collection to perpetrating phishing attacks.
DNS-over-HTTPS (DoH) encapsulates standard DNS requests into encrypted HTTPS requests, hiding the contents of the requests from third parties. DoH requests are sent to a trusted DoH resolver endpoint, and DNS resolution is sent back to the client via the same encrypted channel. A significant benefit of DoH is its simplicity. DoH is applied without requiring any changes to the originating client application. DoH works on any network that allows Internet traffic and does not require any special configuration.
The importance of encrypting DNS traffic
The DNS system was designed with scalability in mind from the beginning through a hierarchical architecture that relies on caching name lookups at different levels of the system. This distributed system has the benefit of affording a global level of scalability, but because the system exchanges information unencrypted, this also leaves it open to attack. The ease of readability allows for eavesdropping and manipulation of the contents of these questions, making DNS a prime target for attackers.
In addition to its plaintext nature, the caching inherent to the DNS hierarchy also leaves it vulnerable to a specific type of attack known as DNS poisoning. With just the right timing—made possible by watching the unencrypted exchange of requests—an attacker can respond with a network address that they control when a user looks up a legitimate domain name. The attacker can then fake a legitimate site, collecting private information without the user’s knowledge until it’s too late.
Caption: Bad actors may spoof network addresses for legitimate names in the DNS system through an attack known as DNS poisoning.
To protect against this and many other types of DNS-based attacks, DNS queries can instead be sent through HTTPS rather than over plaintext, unvalidated UDP. This is the role that DNS over HTTPS (DoH) plays by encrypting DNS queries through encapsulation in an HTTPS request and sending them to a trusted DoH resolver. Hiding DNS queries from view is like taking a postcard, inserting it inside an envelope, and sealing it shut. DNS traffic is also hidden among other HTTPS traffic to websites and web apps, so packets can’t be as easily identified.
DNS-over-HTTPS (DoH) hides DNS traffic from view, preventing most types of DNS-based attacks.
Introducing device-wide DNS encryption with Twingate
Most modern browsers offer automatic DoH protection to trusted DoH resolvers, but DNS requests on devices are not isolated to browsers. This leaves a gap in DNS protection that Twingate is uniquely positioned to fill. The Twingate client provides configuration-less private DNS resolution, making it possible to offer automatic DoH protection for all DNS traffic on a device (for details, see how DNS works with Twingate). Not only browser-originated DNS requests are automatically encrypted—any DNS request on a user’s device, regardless of the application, gets encrypted.
The benefits of encrypting DNS traffic by default are clear, and rather than relying on application-specific configurations for DoH, such as browser-based DoH, Twingate now provides blanket DNS encryption for all DNS traffic on a device.

Secure DNS is enforced on any user running the Twingate Client. Twingate admins can select the DoH resolver of their choice, such as Cloudflare, Google, OpenDNS, or custom. DoH policy can be set where all DNS traffic must be encrypted for always-on protection, or as an automatic failover mode where Twingate uses regular DNS if we can’t contact the DoH resolver.
DoH applied universally across all systems and resources enforces a comprehensive defense-in-depth strategy for today’s cybersecurity threats. This system-wide DoH capability opens up new possibilities for DNS security by using the Twingate client to route DNS requests to common DNS security tools like NextDNS, Cloudflare Gateway, and others. There’s no need to install a separate, dedicated DNS security agent on the device.
This means a single Twingate client can be configured to provide private access to resources as well as secure public internet traffic, so you can leverage existing DNS filtering products to:
Apply DNS-level threat filtering against known malware and phishing sites often initiated by unsuspecting employees
Block employee access to undesirable or inappropriate content
Provide visibility into the applications employees are using to uncover potential shadow IT
Improve employee experience by blocking ads and trackers on websites
Ensure home ISPs or public wifis can’t view visited sites
Read more about this new functionality in our docs and watch a short demo of Twingate Secure DNS in action on YouTube.
Try it for free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Announcing Secure DNS with Twingate
Alex Marshall
•
•
Aug 2, 2022

Businesses around the world are in the midst of a tectonic shift to support a work-from-anywhere workforce without sacrificing company security. Our customers tell us their IT and security teams are grappling with how to provide employees with the same ease of use they experienced when working inside a heavily protected office network. Achieving a balance of security and usability when employees are accessing both public and private resources from hundreds of individual networks all over the world is a major challenge.
A critical component of a modern security strategy is protecting internet traffic. We’re excited to announce Twingate’s very first capability to protect and encrypt not just users’ private traffic, but also the most common unencrypted traffic that flows over networks today: DNS.
The history of the Domain Name System
The Domain Name System was established in 1983 and traces its roots back to the proto-Internet, ARPANET. DNS is the global name translation system for the internet that converts human-readable network addresses such as www.google.com into machine-readable IP addresses such as “172.253.124.147‚ or “2607:f8b0:4004:c06::67‚ that networks use to route traffic from source to destination.
The DNS system converts human-readable addresses into network addresses through a distributed, hierarchical system.
Although there have been some security improvements recently, such as DNSSEC, the vast majority of DNS requests are still unencrypted and hence vulnerable to a range of exploits from data collection to perpetrating phishing attacks.
DNS-over-HTTPS (DoH) encapsulates standard DNS requests into encrypted HTTPS requests, hiding the contents of the requests from third parties. DoH requests are sent to a trusted DoH resolver endpoint, and DNS resolution is sent back to the client via the same encrypted channel. A significant benefit of DoH is its simplicity. DoH is applied without requiring any changes to the originating client application. DoH works on any network that allows Internet traffic and does not require any special configuration.
The importance of encrypting DNS traffic
The DNS system was designed with scalability in mind from the beginning through a hierarchical architecture that relies on caching name lookups at different levels of the system. This distributed system has the benefit of affording a global level of scalability, but because the system exchanges information unencrypted, this also leaves it open to attack. The ease of readability allows for eavesdropping and manipulation of the contents of these questions, making DNS a prime target for attackers.
In addition to its plaintext nature, the caching inherent to the DNS hierarchy also leaves it vulnerable to a specific type of attack known as DNS poisoning. With just the right timing—made possible by watching the unencrypted exchange of requests—an attacker can respond with a network address that they control when a user looks up a legitimate domain name. The attacker can then fake a legitimate site, collecting private information without the user’s knowledge until it’s too late.
Caption: Bad actors may spoof network addresses for legitimate names in the DNS system through an attack known as DNS poisoning.
To protect against this and many other types of DNS-based attacks, DNS queries can instead be sent through HTTPS rather than over plaintext, unvalidated UDP. This is the role that DNS over HTTPS (DoH) plays by encrypting DNS queries through encapsulation in an HTTPS request and sending them to a trusted DoH resolver. Hiding DNS queries from view is like taking a postcard, inserting it inside an envelope, and sealing it shut. DNS traffic is also hidden among other HTTPS traffic to websites and web apps, so packets can’t be as easily identified.
DNS-over-HTTPS (DoH) hides DNS traffic from view, preventing most types of DNS-based attacks.
Introducing device-wide DNS encryption with Twingate
Most modern browsers offer automatic DoH protection to trusted DoH resolvers, but DNS requests on devices are not isolated to browsers. This leaves a gap in DNS protection that Twingate is uniquely positioned to fill. The Twingate client provides configuration-less private DNS resolution, making it possible to offer automatic DoH protection for all DNS traffic on a device (for details, see how DNS works with Twingate). Not only browser-originated DNS requests are automatically encrypted—any DNS request on a user’s device, regardless of the application, gets encrypted.
The benefits of encrypting DNS traffic by default are clear, and rather than relying on application-specific configurations for DoH, such as browser-based DoH, Twingate now provides blanket DNS encryption for all DNS traffic on a device.

Secure DNS is enforced on any user running the Twingate Client. Twingate admins can select the DoH resolver of their choice, such as Cloudflare, Google, OpenDNS, or custom. DoH policy can be set where all DNS traffic must be encrypted for always-on protection, or as an automatic failover mode where Twingate uses regular DNS if we can’t contact the DoH resolver.
DoH applied universally across all systems and resources enforces a comprehensive defense-in-depth strategy for today’s cybersecurity threats. This system-wide DoH capability opens up new possibilities for DNS security by using the Twingate client to route DNS requests to common DNS security tools like NextDNS, Cloudflare Gateway, and others. There’s no need to install a separate, dedicated DNS security agent on the device.
This means a single Twingate client can be configured to provide private access to resources as well as secure public internet traffic, so you can leverage existing DNS filtering products to:
Apply DNS-level threat filtering against known malware and phishing sites often initiated by unsuspecting employees
Block employee access to undesirable or inappropriate content
Provide visibility into the applications employees are using to uncover potential shadow IT
Improve employee experience by blocking ads and trackers on websites
Ensure home ISPs or public wifis can’t view visited sites
Read more about this new functionality in our docs and watch a short demo of Twingate Secure DNS in action on YouTube.
Try it for free today!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions