The Best 10 Alternatives to Cylance (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024
Cylance offers AI-driven cybersecurity solutions, including managed detection and response, endpoint security, and zero trust connectivity. While effective, Cylance may not suit every organization's needs. This article explores how Twingate's zero trust networking model provides secure access for distributed workforces.
10 Alternatives to Cylance
1. Crowdstrike
CrowdStrike is a cybersecurity solution designed to prevent breaches using AI-native technology. It offers comprehensive protection for endpoints, cloud environments, and identities. With a focus on ease of use and scalability, CrowdStrike aims to provide a secure and maintainable solution for businesses of all sizes.
Crowdstrike Pricing
Falcon Pro (Enterprise): $99.99/device per year
Falcon Enterprise: $184.99/device per year
Falcon Elite: Contact sales for pricing
Falcon Go (Small Business): $59.99/device per year
Falcon Pro (Small Business): $99.99/device per year
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
CrowdStrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users praise its advanced threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
Advanced Threat Detection: CrowdStrike's AI-native platform excels in identifying and mitigating threats swiftly, ensuring robust security for diverse environments.
Ease of Use: Users appreciate the intuitive interface, which simplifies complex security tasks, making it accessible even for those less familiar with cybersecurity.
Comprehensive Security: The platform offers extensive protection across endpoints, identities, and cloud environments, providing a unified security solution.
Cons:
High Cost: The advanced features and comprehensive solutions come at a premium price, potentially limiting accessibility for smaller businesses.
Complexity: Despite its user-friendly interface, the wide range of features can be overwhelming for some users to fully utilize.
False Positives: The heavy reliance on AI can sometimes result in false positives, requiring continuous monitoring and adjustments.
2. Ivanti Endpoint Security
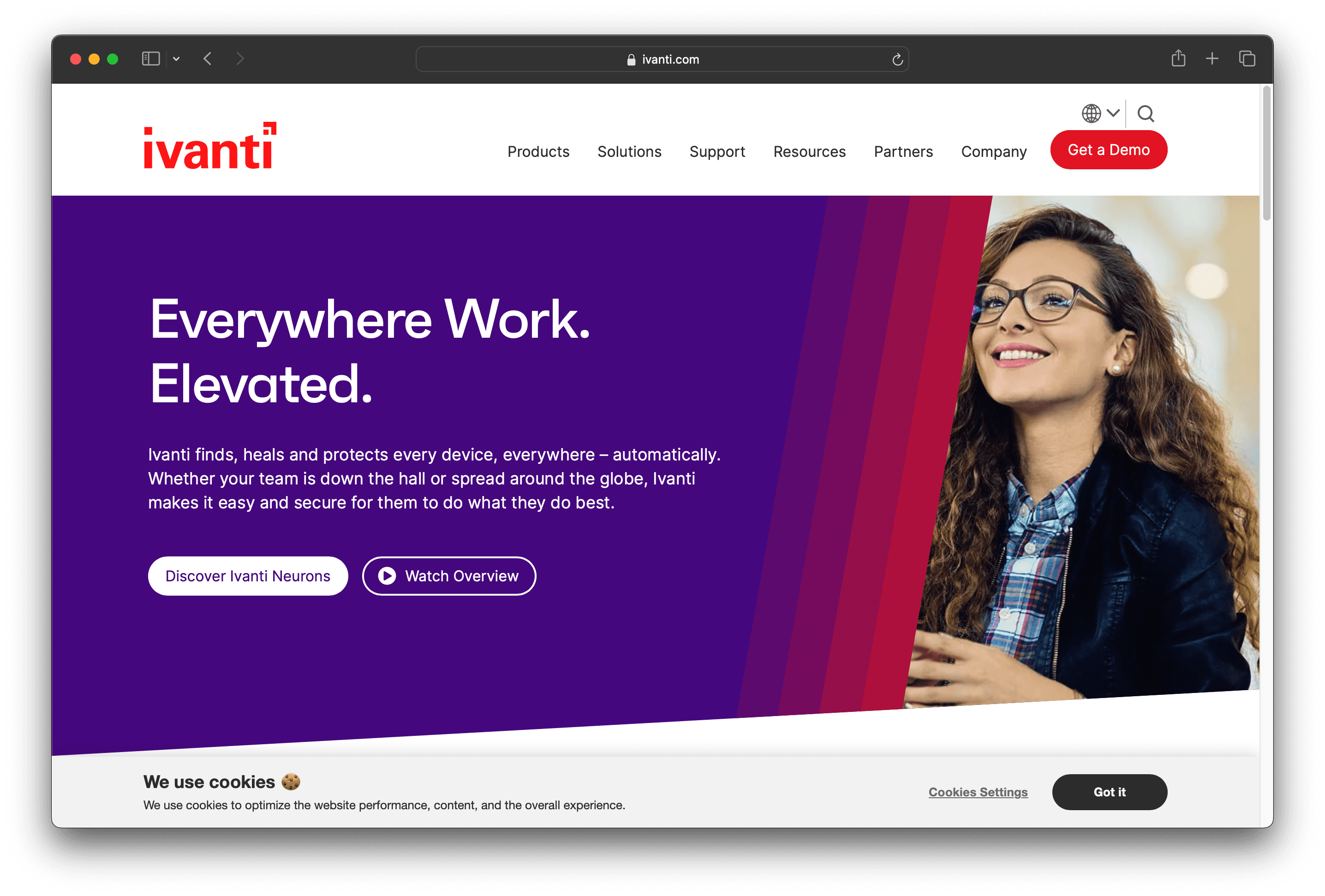
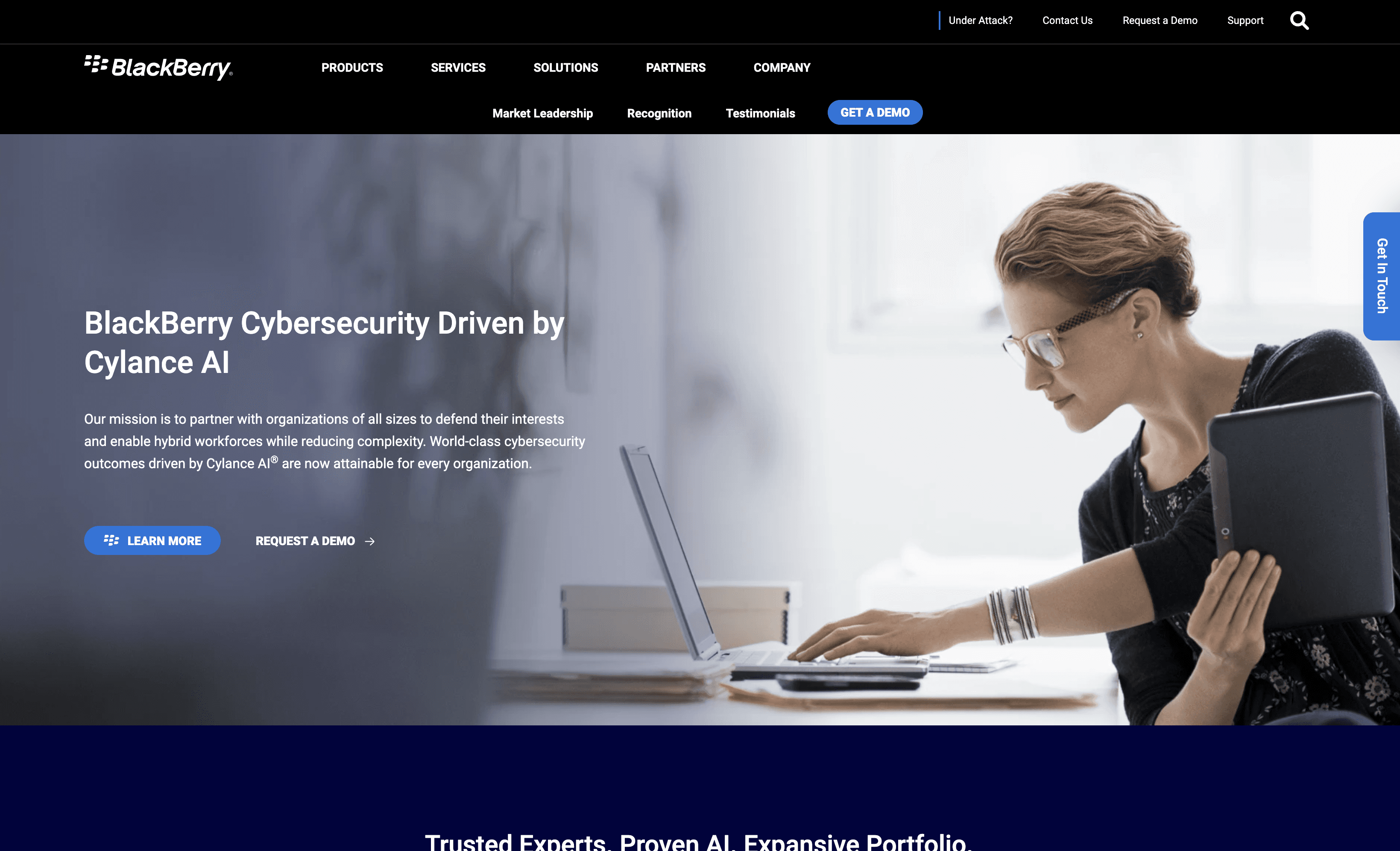
Ivanti Endpoint Security is designed to protect and manage endpoints, offering features like risk-based patch management and mobile threat defense. It aims to secure devices from cyber threats while ensuring ease of use and scalability, making it a practical solution for businesses of all sizes.
Ivanti Endpoint Security Pricing
ITSM Professional
ITSM Premium
ITSM Enterprise
ITSM Enterprise Premium
Secure UEM Professional
Secure UEM Professional Plus
Secure UEM Premium
Ivanti Endpoint Security's pricing is not public. Contact their support for more info.
Ivanti Endpoint Security Reviews
Ivanti Endpoint Security has an overall rating of 4.3 out of 5 stars based on 17 reviews. Users appreciate its ease of use and excellent customer service. Check out more of our reviews here!
Pros and Cons ofIvanti Endpoint Security
Pros:
Comprehensive Protection: Shields against ransomware, phishing, and other threats across diverse devices and environments.
Risk-Based Patch Management: Prioritizes critical patches, ensuring effective endpoint security.
Mobile Threat Defense: Provides real-time, zero-day threat protection for mobile devices.
Cons:
Complexity: Managing and securing a wide range of devices and applications requires significant effort and expertise.
Integration: Integrating with existing systems and workflows, especially in large organizations, can be challenging.
Cost: Comprehensive security solutions can be expensive, potentially limiting accessibility for smaller organizations.
3. Trend Vision One
Trend Vision One is a comprehensive endpoint security solution by Trend Micro. It consolidates endpoint, server, and workload security into a single platform, offering centralized visibility and response. Designed for ease of use and scalability, it aims to protect businesses from advanced threats across various environments.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its comprehensive threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Centralized Management: Offers a unified view for managing security across endpoints, servers, and cloud workloads, enhancing operational efficiency.
Comprehensive Threat Detection: Integrates EDR and XDR capabilities, providing extensive protection across various security layers.
Layered Security: Delivers multiple layers of protection, including industry-leading intrusion prevention and proactive vulnerability protection.
Cons:
Complexity: The comprehensive nature of the solution may require significant expertise and resources to manage effectively.
Cost: Advanced features and 24/7 monitoring services could be expensive, potentially limiting accessibility for smaller organizations.
Integration: Integrating such a robust solution into existing IT infrastructure might be challenging and time-consuming.
4. Cisco Secure Endpoint

Cisco Secure Endpoint is a cloud-native solution designed to provide advanced endpoint security. It focuses on quick detection, response, and recovery from attacks, aiming to reduce remediation times significantly. With seamless integration into existing infrastructure, it offers a user-friendly and scalable security solution for businesses of all sizes.
Cisco Secure Endpoint Pricing
Cisco Secure Endpoint's pricing is not public. Contact their support for more info.
Cisco Secure Endpoint Reviews
Cisco Secure Endpoint has an overall rating of 4.5 out of 5 stars based on 21 reviews. Users appreciate its comprehensive protection and ease of use. Check out more of our reviews here!
Pros and Cons of Cisco Secure Endpoint
Pros:
Speed in Detection and Response: Reduces remediation times by up to 85%, ensuring swift action against threats.
Advanced EDR Capabilities: Includes built-in or managed endpoint detection and response, threat hunting, and risk-based vulnerability management.
Streamlined Investigations: Orbital Advanced Search capability provides quick answers about endpoints, enhancing efficiency.
Cons:
Compatibility Issues: Some users report challenges with integrating the solution into existing systems.
Inaccurate Information: Occasional discrepancies in threat detection data require manual verification.
Limited OS Compatibility: The solution may not support all operating systems, limiting its applicability.
5. Hexnode UEM
Hexnode UEM is a unified endpoint management solution designed to simplify device management across various platforms. It offers features like security management, remote control, and app management, aiming to provide a seamless and scalable solution for businesses of all sizes. Hexnode focuses on ease of use and comprehensive support.
Hexnode UEM Pricing
Hexnode UEM's pricing is not public. Contact their support for more info.
Hexnode UEM Reviews
Hexnode UEM has an overall rating of 4.6 out of 5 stars based on 189 reviews. Users appreciate its intuitive interface and comprehensive device management. Check out more of our reviews here!
Pros and Cons of Hexnode UEM
Pros:
Comprehensive Device Management: Hexnode UEM supports a wide range of platforms, including Windows, macOS, Android, iOS, and more, ensuring versatile device management.
Security Features: Offers robust security policies, including BitLocker management and password rules, providing enterprise-grade protection for all devices.
Ease of Use: Users appreciate the intuitive interface, which simplifies complex device management tasks, making it accessible even for those less familiar with UEM solutions.
Cons:
Complexity for New Users: The extensive range of features can be overwhelming for new users, requiring significant time to master.
Potential Cost: Comprehensive UEM solutions can be expensive, which might be a concern for small businesses with limited budgets.
Learning Curve: The need for detailed product training and documentation suggests a significant learning curve, especially for those new to UEM.
6. Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is a security solution designed to protect endpoints across various platforms. It offers AI-powered detection and response, global threat intelligence, and comprehensive protection for devices, including Windows, macOS, Linux, Android, iOS, and IoT. The solution aims to provide robust security and ease of use for businesses of all sizes.
Microsoft Defender for Endpoint Pricing
Microsoft Defender for Endpoint P1: Included with Microsoft 365 E3
Microsoft Defender for Endpoint P2: Included with Microsoft 365 E5
Microsoft Defender for Endpoint Reviews
Microsoft Defender for Endpoint has an overall rating of 4.4 out of 5 stars based on 303 reviews. Users appreciate its comprehensive security features and ease of use. Check out more of our reviews here!
Pros and Cons of Microsoft Defender for Endpoint
Pros:
Multiplatform Support: Protects Windows, macOS, Linux, Android, iOS, and IoT devices, ensuring comprehensive security across diverse environments.
AI-Powered Security: Utilizes artificial intelligence to detect and mitigate cyber threats like ransomware, enhancing the security team's efficiency.
Global Threat Intelligence: Offers a clear view of the cyberattack landscape, providing actionable insights and best practices for prevention.
Cons:
Complexity: Managing and configuring the solution effectively may require significant expertise and resources.
Resource Intensive: The comprehensive security features can potentially impact system performance, especially on older devices.
Cost: Higher price point compared to some other endpoint protection solutions, which might be a concern for small businesses.
7. WatchGuard Endpoint Security
WatchGuard Endpoint Security is a comprehensive solution designed to protect devices from advanced cyber threats. It offers features like Endpoint Detection & Response (EDR), next-gen antivirus, and DNS filtering. With a focus on ease of use and scalability, it aims to provide robust security for businesses of all sizes.
WatchGuard Endpoint Security Pricing
WatchGuard Endpoint Security's pricing is not public. Contact their support for more info.
WatchGuard Endpoint Security Reviews
WatchGuard Endpoint Security has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its ease of use and comprehensive protection. Check out more of our reviews here!
Pros and Cons of WatchGuard Endpoint Security
Pros:
Comprehensive Protection: Integrates next-gen antivirus, EDR, and DNS filtering, ensuring robust defense against diverse cyber threats.
Unified Security Platform: Provides seamless protection for networks, endpoints, Wi-Fi, and identities, enhancing overall security posture.
Cloud-Based Management: Streamlines security administration with a user-friendly interface, centralizing control and reporting.
Cons:
Complexity: The integrated nature of the platform may require a steep learning curve for new users.
Dependency on Cloud: Heavy reliance on cloud-based management might limit use for organizations with strict on-premises requirements.
Potential Cost: The full stack of integrated modules and advanced features might be cost-prohibitive for smaller organizations.
8. Huntress Managed EDR
Huntress Managed EDR is a cybersecurity solution designed to provide comprehensive endpoint detection and response. It focuses on ease of deployment and scalability, making it ideal for small and medium-sized businesses and IT providers. With 24/7 monitoring and expert support, Huntress aims to protect endpoints effectively and efficiently.
Huntress Managed EDR Pricing
Huntress Managed EDR's pricing is not public. Contact their support for more info.
Huntress Managed EDR Reviews
Huntress Managed EDR has an overall rating of 4.9 out of 5 stars based on 663 reviews. Users praise its excellent customer support and ease of use. Check out more of our reviews here!
Pros and Cons of Huntress Managed EDR
Pros:
Customer Support: Users consistently praise Huntress for its responsive and knowledgeable customer support team, ensuring quick resolutions to issues.
Ease of Use: The platform is user-friendly, making it accessible even for those with limited cybersecurity expertise.
Threat Detection: Huntress excels in identifying and mitigating threats, providing robust protection for endpoints.
Cons:
False Positives: Some users report occasional false positives, which can require additional time to investigate and resolve.
Defender Dependence: The platform's effectiveness can be limited by its reliance on Microsoft Defender, potentially impacting non-Windows environments.
Expensive: The cost of the service may be prohibitive for smaller businesses with limited budgets.
9. Kaspersky Endpoint Security Cloud
Kaspersky Endpoint Security Cloud is a cybersecurity solution designed for small to medium-sized businesses. It offers comprehensive protection, ease of use, and seamless deployment. With features like malware protection, ransomware prevention, and cloud security, it aims to provide robust and scalable security for diverse business environments.
Kaspersky Endpoint Security Cloud Pricing
Kaspersky Endpoint Security Cloud's pricing is not public. Contact their support for more info.
Kaspersky Endpoint Security Cloud Reviews
Kaspersky Endpoint Security Cloud has an overall rating of 4.3 out of 5 stars based on 217 reviews. Users appreciate its comprehensive protection but note it can be resource-intensive. Check out more of our reviews here!
Pros and Cons of Kaspersky Endpoint Security Cloud
Pros:
Affordable and Easy to Install: Designed for small to medium-sized businesses, it offers a cost-effective solution that's quick to set up.
Comprehensive Protection: Provides robust defense against malware, ransomware, and other cyber threats, ensuring data security.
Cloud-Based Management: Simplifies security administration with a user-friendly interface, requiring minimal time for management.
Cons:
High Resource Usage: The software can be resource-intensive, potentially slowing down older systems.
Internet Dependence: Requires a stable internet connection for cloud management, which may be a limitation for some users.
Learning Curve: Users unfamiliar with cybersecurity tools may find the initial setup and configuration challenging.
10. NinjaOne

NinjaOne is an IT management solution designed to manage, secure, and support all endpoints. It offers features like endpoint management, remote access, and patch management. With a focus on ease of use and efficiency, NinjaOne aims to provide a secure and scalable solution for businesses of all sizes.
NinjaOne Pricing
NinjaOne's pricing is not public. Contact their support for more info.
NinjaOne Reviews
NinjaOne has an overall rating of 4.8 out of 5 stars based on 1,437 reviews. Users appreciate its ease of use and comprehensive features. Check out more of our reviews here!
Pros and Cons of NinjaOne
Pros:
Comprehensive Endpoint Management: Provides visibility and control over endpoints, supporting various operating systems and devices.
Ease of Use: Quick to implement, easy to learn, and intuitive to use, making it accessible for all skill levels.
Automation: Automates repetitive tasks, freeing up IT teams for more strategic work and improving overall efficiency.
Cons:
Complexity for Small Teams: The extensive features might be overwhelming for smaller IT teams, requiring significant time to master.
Cost: Comprehensive solutions like NinjaOne can be expensive, which might be a consideration for smaller businesses.
Learning Curve: Despite being user-friendly, there might still be a learning curve for new users to fully leverage all features.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern work landscape. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to Cylance (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024

Cylance offers AI-driven cybersecurity solutions, including managed detection and response, endpoint security, and zero trust connectivity. While effective, Cylance may not suit every organization's needs. This article explores how Twingate's zero trust networking model provides secure access for distributed workforces.

10 Alternatives to Cylance
1. Crowdstrike

CrowdStrike is a cybersecurity solution designed to prevent breaches using AI-native technology. It offers comprehensive protection for endpoints, cloud environments, and identities. With a focus on ease of use and scalability, CrowdStrike aims to provide a secure and maintainable solution for businesses of all sizes.
Crowdstrike Pricing
Falcon Pro (Enterprise): $99.99/device per year
Falcon Enterprise: $184.99/device per year
Falcon Elite: Contact sales for pricing
Falcon Go (Small Business): $59.99/device per year
Falcon Pro (Small Business): $99.99/device per year
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
CrowdStrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users praise its advanced threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
Advanced Threat Detection: CrowdStrike's AI-native platform excels in identifying and mitigating threats swiftly, ensuring robust security for diverse environments.
Ease of Use: Users appreciate the intuitive interface, which simplifies complex security tasks, making it accessible even for those less familiar with cybersecurity.
Comprehensive Security: The platform offers extensive protection across endpoints, identities, and cloud environments, providing a unified security solution.
Cons:
High Cost: The advanced features and comprehensive solutions come at a premium price, potentially limiting accessibility for smaller businesses.
Complexity: Despite its user-friendly interface, the wide range of features can be overwhelming for some users to fully utilize.
False Positives: The heavy reliance on AI can sometimes result in false positives, requiring continuous monitoring and adjustments.
2. Ivanti Endpoint Security

Ivanti Endpoint Security is designed to protect and manage endpoints, offering features like risk-based patch management and mobile threat defense. It aims to secure devices from cyber threats while ensuring ease of use and scalability, making it a practical solution for businesses of all sizes.
Ivanti Endpoint Security Pricing
ITSM Professional
ITSM Premium
ITSM Enterprise
ITSM Enterprise Premium
Secure UEM Professional
Secure UEM Professional Plus
Secure UEM Premium
Ivanti Endpoint Security's pricing is not public. Contact their support for more info.
Ivanti Endpoint Security Reviews
Ivanti Endpoint Security has an overall rating of 4.3 out of 5 stars based on 17 reviews. Users appreciate its ease of use and excellent customer service. Check out more of our reviews here!
Pros and Cons ofIvanti Endpoint Security
Pros:
Comprehensive Protection: Shields against ransomware, phishing, and other threats across diverse devices and environments.
Risk-Based Patch Management: Prioritizes critical patches, ensuring effective endpoint security.
Mobile Threat Defense: Provides real-time, zero-day threat protection for mobile devices.
Cons:
Complexity: Managing and securing a wide range of devices and applications requires significant effort and expertise.
Integration: Integrating with existing systems and workflows, especially in large organizations, can be challenging.
Cost: Comprehensive security solutions can be expensive, potentially limiting accessibility for smaller organizations.
3. Trend Vision One

Trend Vision One is a comprehensive endpoint security solution by Trend Micro. It consolidates endpoint, server, and workload security into a single platform, offering centralized visibility and response. Designed for ease of use and scalability, it aims to protect businesses from advanced threats across various environments.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its comprehensive threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Centralized Management: Offers a unified view for managing security across endpoints, servers, and cloud workloads, enhancing operational efficiency.
Comprehensive Threat Detection: Integrates EDR and XDR capabilities, providing extensive protection across various security layers.
Layered Security: Delivers multiple layers of protection, including industry-leading intrusion prevention and proactive vulnerability protection.
Cons:
Complexity: The comprehensive nature of the solution may require significant expertise and resources to manage effectively.
Cost: Advanced features and 24/7 monitoring services could be expensive, potentially limiting accessibility for smaller organizations.
Integration: Integrating such a robust solution into existing IT infrastructure might be challenging and time-consuming.
4. Cisco Secure Endpoint

Cisco Secure Endpoint is a cloud-native solution designed to provide advanced endpoint security. It focuses on quick detection, response, and recovery from attacks, aiming to reduce remediation times significantly. With seamless integration into existing infrastructure, it offers a user-friendly and scalable security solution for businesses of all sizes.
Cisco Secure Endpoint Pricing
Cisco Secure Endpoint's pricing is not public. Contact their support for more info.
Cisco Secure Endpoint Reviews
Cisco Secure Endpoint has an overall rating of 4.5 out of 5 stars based on 21 reviews. Users appreciate its comprehensive protection and ease of use. Check out more of our reviews here!
Pros and Cons of Cisco Secure Endpoint
Pros:
Speed in Detection and Response: Reduces remediation times by up to 85%, ensuring swift action against threats.
Advanced EDR Capabilities: Includes built-in or managed endpoint detection and response, threat hunting, and risk-based vulnerability management.
Streamlined Investigations: Orbital Advanced Search capability provides quick answers about endpoints, enhancing efficiency.
Cons:
Compatibility Issues: Some users report challenges with integrating the solution into existing systems.
Inaccurate Information: Occasional discrepancies in threat detection data require manual verification.
Limited OS Compatibility: The solution may not support all operating systems, limiting its applicability.
5. Hexnode UEM

Hexnode UEM is a unified endpoint management solution designed to simplify device management across various platforms. It offers features like security management, remote control, and app management, aiming to provide a seamless and scalable solution for businesses of all sizes. Hexnode focuses on ease of use and comprehensive support.
Hexnode UEM Pricing
Hexnode UEM's pricing is not public. Contact their support for more info.
Hexnode UEM Reviews
Hexnode UEM has an overall rating of 4.6 out of 5 stars based on 189 reviews. Users appreciate its intuitive interface and comprehensive device management. Check out more of our reviews here!
Pros and Cons of Hexnode UEM
Pros:
Comprehensive Device Management: Hexnode UEM supports a wide range of platforms, including Windows, macOS, Android, iOS, and more, ensuring versatile device management.
Security Features: Offers robust security policies, including BitLocker management and password rules, providing enterprise-grade protection for all devices.
Ease of Use: Users appreciate the intuitive interface, which simplifies complex device management tasks, making it accessible even for those less familiar with UEM solutions.
Cons:
Complexity for New Users: The extensive range of features can be overwhelming for new users, requiring significant time to master.
Potential Cost: Comprehensive UEM solutions can be expensive, which might be a concern for small businesses with limited budgets.
Learning Curve: The need for detailed product training and documentation suggests a significant learning curve, especially for those new to UEM.
6. Microsoft Defender for Endpoint

Microsoft Defender for Endpoint is a security solution designed to protect endpoints across various platforms. It offers AI-powered detection and response, global threat intelligence, and comprehensive protection for devices, including Windows, macOS, Linux, Android, iOS, and IoT. The solution aims to provide robust security and ease of use for businesses of all sizes.
Microsoft Defender for Endpoint Pricing
Microsoft Defender for Endpoint P1: Included with Microsoft 365 E3
Microsoft Defender for Endpoint P2: Included with Microsoft 365 E5
Microsoft Defender for Endpoint Reviews
Microsoft Defender for Endpoint has an overall rating of 4.4 out of 5 stars based on 303 reviews. Users appreciate its comprehensive security features and ease of use. Check out more of our reviews here!
Pros and Cons of Microsoft Defender for Endpoint
Pros:
Multiplatform Support: Protects Windows, macOS, Linux, Android, iOS, and IoT devices, ensuring comprehensive security across diverse environments.
AI-Powered Security: Utilizes artificial intelligence to detect and mitigate cyber threats like ransomware, enhancing the security team's efficiency.
Global Threat Intelligence: Offers a clear view of the cyberattack landscape, providing actionable insights and best practices for prevention.
Cons:
Complexity: Managing and configuring the solution effectively may require significant expertise and resources.
Resource Intensive: The comprehensive security features can potentially impact system performance, especially on older devices.
Cost: Higher price point compared to some other endpoint protection solutions, which might be a concern for small businesses.
7. WatchGuard Endpoint Security

WatchGuard Endpoint Security is a comprehensive solution designed to protect devices from advanced cyber threats. It offers features like Endpoint Detection & Response (EDR), next-gen antivirus, and DNS filtering. With a focus on ease of use and scalability, it aims to provide robust security for businesses of all sizes.
WatchGuard Endpoint Security Pricing
WatchGuard Endpoint Security's pricing is not public. Contact their support for more info.
WatchGuard Endpoint Security Reviews
WatchGuard Endpoint Security has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its ease of use and comprehensive protection. Check out more of our reviews here!
Pros and Cons of WatchGuard Endpoint Security
Pros:
Comprehensive Protection: Integrates next-gen antivirus, EDR, and DNS filtering, ensuring robust defense against diverse cyber threats.
Unified Security Platform: Provides seamless protection for networks, endpoints, Wi-Fi, and identities, enhancing overall security posture.
Cloud-Based Management: Streamlines security administration with a user-friendly interface, centralizing control and reporting.
Cons:
Complexity: The integrated nature of the platform may require a steep learning curve for new users.
Dependency on Cloud: Heavy reliance on cloud-based management might limit use for organizations with strict on-premises requirements.
Potential Cost: The full stack of integrated modules and advanced features might be cost-prohibitive for smaller organizations.
8. Huntress Managed EDR

Huntress Managed EDR is a cybersecurity solution designed to provide comprehensive endpoint detection and response. It focuses on ease of deployment and scalability, making it ideal for small and medium-sized businesses and IT providers. With 24/7 monitoring and expert support, Huntress aims to protect endpoints effectively and efficiently.
Huntress Managed EDR Pricing
Huntress Managed EDR's pricing is not public. Contact their support for more info.
Huntress Managed EDR Reviews
Huntress Managed EDR has an overall rating of 4.9 out of 5 stars based on 663 reviews. Users praise its excellent customer support and ease of use. Check out more of our reviews here!
Pros and Cons of Huntress Managed EDR
Pros:
Customer Support: Users consistently praise Huntress for its responsive and knowledgeable customer support team, ensuring quick resolutions to issues.
Ease of Use: The platform is user-friendly, making it accessible even for those with limited cybersecurity expertise.
Threat Detection: Huntress excels in identifying and mitigating threats, providing robust protection for endpoints.
Cons:
False Positives: Some users report occasional false positives, which can require additional time to investigate and resolve.
Defender Dependence: The platform's effectiveness can be limited by its reliance on Microsoft Defender, potentially impacting non-Windows environments.
Expensive: The cost of the service may be prohibitive for smaller businesses with limited budgets.
9. Kaspersky Endpoint Security Cloud

Kaspersky Endpoint Security Cloud is a cybersecurity solution designed for small to medium-sized businesses. It offers comprehensive protection, ease of use, and seamless deployment. With features like malware protection, ransomware prevention, and cloud security, it aims to provide robust and scalable security for diverse business environments.
Kaspersky Endpoint Security Cloud Pricing
Kaspersky Endpoint Security Cloud's pricing is not public. Contact their support for more info.
Kaspersky Endpoint Security Cloud Reviews
Kaspersky Endpoint Security Cloud has an overall rating of 4.3 out of 5 stars based on 217 reviews. Users appreciate its comprehensive protection but note it can be resource-intensive. Check out more of our reviews here!
Pros and Cons of Kaspersky Endpoint Security Cloud
Pros:
Affordable and Easy to Install: Designed for small to medium-sized businesses, it offers a cost-effective solution that's quick to set up.
Comprehensive Protection: Provides robust defense against malware, ransomware, and other cyber threats, ensuring data security.
Cloud-Based Management: Simplifies security administration with a user-friendly interface, requiring minimal time for management.
Cons:
High Resource Usage: The software can be resource-intensive, potentially slowing down older systems.
Internet Dependence: Requires a stable internet connection for cloud management, which may be a limitation for some users.
Learning Curve: Users unfamiliar with cybersecurity tools may find the initial setup and configuration challenging.
10. NinjaOne

NinjaOne is an IT management solution designed to manage, secure, and support all endpoints. It offers features like endpoint management, remote access, and patch management. With a focus on ease of use and efficiency, NinjaOne aims to provide a secure and scalable solution for businesses of all sizes.
NinjaOne Pricing
NinjaOne's pricing is not public. Contact their support for more info.
NinjaOne Reviews
NinjaOne has an overall rating of 4.8 out of 5 stars based on 1,437 reviews. Users appreciate its ease of use and comprehensive features. Check out more of our reviews here!
Pros and Cons of NinjaOne
Pros:
Comprehensive Endpoint Management: Provides visibility and control over endpoints, supporting various operating systems and devices.
Ease of Use: Quick to implement, easy to learn, and intuitive to use, making it accessible for all skill levels.
Automation: Automates repetitive tasks, freeing up IT teams for more strategic work and improving overall efficiency.
Cons:
Complexity for Small Teams: The extensive features might be overwhelming for smaller IT teams, requiring significant time to master.
Cost: Comprehensive solutions like NinjaOne can be expensive, which might be a consideration for smaller businesses.
Learning Curve: Despite being user-friendly, there might still be a learning curve for new users to fully leverage all features.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern work landscape. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to Cylance (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024

Cylance offers AI-driven cybersecurity solutions, including managed detection and response, endpoint security, and zero trust connectivity. While effective, Cylance may not suit every organization's needs. This article explores how Twingate's zero trust networking model provides secure access for distributed workforces.

10 Alternatives to Cylance
1. Crowdstrike

CrowdStrike is a cybersecurity solution designed to prevent breaches using AI-native technology. It offers comprehensive protection for endpoints, cloud environments, and identities. With a focus on ease of use and scalability, CrowdStrike aims to provide a secure and maintainable solution for businesses of all sizes.
Crowdstrike Pricing
Falcon Pro (Enterprise): $99.99/device per year
Falcon Enterprise: $184.99/device per year
Falcon Elite: Contact sales for pricing
Falcon Go (Small Business): $59.99/device per year
Falcon Pro (Small Business): $99.99/device per year
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
CrowdStrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users praise its advanced threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
Advanced Threat Detection: CrowdStrike's AI-native platform excels in identifying and mitigating threats swiftly, ensuring robust security for diverse environments.
Ease of Use: Users appreciate the intuitive interface, which simplifies complex security tasks, making it accessible even for those less familiar with cybersecurity.
Comprehensive Security: The platform offers extensive protection across endpoints, identities, and cloud environments, providing a unified security solution.
Cons:
High Cost: The advanced features and comprehensive solutions come at a premium price, potentially limiting accessibility for smaller businesses.
Complexity: Despite its user-friendly interface, the wide range of features can be overwhelming for some users to fully utilize.
False Positives: The heavy reliance on AI can sometimes result in false positives, requiring continuous monitoring and adjustments.
2. Ivanti Endpoint Security

Ivanti Endpoint Security is designed to protect and manage endpoints, offering features like risk-based patch management and mobile threat defense. It aims to secure devices from cyber threats while ensuring ease of use and scalability, making it a practical solution for businesses of all sizes.
Ivanti Endpoint Security Pricing
ITSM Professional
ITSM Premium
ITSM Enterprise
ITSM Enterprise Premium
Secure UEM Professional
Secure UEM Professional Plus
Secure UEM Premium
Ivanti Endpoint Security's pricing is not public. Contact their support for more info.
Ivanti Endpoint Security Reviews
Ivanti Endpoint Security has an overall rating of 4.3 out of 5 stars based on 17 reviews. Users appreciate its ease of use and excellent customer service. Check out more of our reviews here!
Pros and Cons ofIvanti Endpoint Security
Pros:
Comprehensive Protection: Shields against ransomware, phishing, and other threats across diverse devices and environments.
Risk-Based Patch Management: Prioritizes critical patches, ensuring effective endpoint security.
Mobile Threat Defense: Provides real-time, zero-day threat protection for mobile devices.
Cons:
Complexity: Managing and securing a wide range of devices and applications requires significant effort and expertise.
Integration: Integrating with existing systems and workflows, especially in large organizations, can be challenging.
Cost: Comprehensive security solutions can be expensive, potentially limiting accessibility for smaller organizations.
3. Trend Vision One

Trend Vision One is a comprehensive endpoint security solution by Trend Micro. It consolidates endpoint, server, and workload security into a single platform, offering centralized visibility and response. Designed for ease of use and scalability, it aims to protect businesses from advanced threats across various environments.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its comprehensive threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Centralized Management: Offers a unified view for managing security across endpoints, servers, and cloud workloads, enhancing operational efficiency.
Comprehensive Threat Detection: Integrates EDR and XDR capabilities, providing extensive protection across various security layers.
Layered Security: Delivers multiple layers of protection, including industry-leading intrusion prevention and proactive vulnerability protection.
Cons:
Complexity: The comprehensive nature of the solution may require significant expertise and resources to manage effectively.
Cost: Advanced features and 24/7 monitoring services could be expensive, potentially limiting accessibility for smaller organizations.
Integration: Integrating such a robust solution into existing IT infrastructure might be challenging and time-consuming.
4. Cisco Secure Endpoint

Cisco Secure Endpoint is a cloud-native solution designed to provide advanced endpoint security. It focuses on quick detection, response, and recovery from attacks, aiming to reduce remediation times significantly. With seamless integration into existing infrastructure, it offers a user-friendly and scalable security solution for businesses of all sizes.
Cisco Secure Endpoint Pricing
Cisco Secure Endpoint's pricing is not public. Contact their support for more info.
Cisco Secure Endpoint Reviews
Cisco Secure Endpoint has an overall rating of 4.5 out of 5 stars based on 21 reviews. Users appreciate its comprehensive protection and ease of use. Check out more of our reviews here!
Pros and Cons of Cisco Secure Endpoint
Pros:
Speed in Detection and Response: Reduces remediation times by up to 85%, ensuring swift action against threats.
Advanced EDR Capabilities: Includes built-in or managed endpoint detection and response, threat hunting, and risk-based vulnerability management.
Streamlined Investigations: Orbital Advanced Search capability provides quick answers about endpoints, enhancing efficiency.
Cons:
Compatibility Issues: Some users report challenges with integrating the solution into existing systems.
Inaccurate Information: Occasional discrepancies in threat detection data require manual verification.
Limited OS Compatibility: The solution may not support all operating systems, limiting its applicability.
5. Hexnode UEM

Hexnode UEM is a unified endpoint management solution designed to simplify device management across various platforms. It offers features like security management, remote control, and app management, aiming to provide a seamless and scalable solution for businesses of all sizes. Hexnode focuses on ease of use and comprehensive support.
Hexnode UEM Pricing
Hexnode UEM's pricing is not public. Contact their support for more info.
Hexnode UEM Reviews
Hexnode UEM has an overall rating of 4.6 out of 5 stars based on 189 reviews. Users appreciate its intuitive interface and comprehensive device management. Check out more of our reviews here!
Pros and Cons of Hexnode UEM
Pros:
Comprehensive Device Management: Hexnode UEM supports a wide range of platforms, including Windows, macOS, Android, iOS, and more, ensuring versatile device management.
Security Features: Offers robust security policies, including BitLocker management and password rules, providing enterprise-grade protection for all devices.
Ease of Use: Users appreciate the intuitive interface, which simplifies complex device management tasks, making it accessible even for those less familiar with UEM solutions.
Cons:
Complexity for New Users: The extensive range of features can be overwhelming for new users, requiring significant time to master.
Potential Cost: Comprehensive UEM solutions can be expensive, which might be a concern for small businesses with limited budgets.
Learning Curve: The need for detailed product training and documentation suggests a significant learning curve, especially for those new to UEM.
6. Microsoft Defender for Endpoint

Microsoft Defender for Endpoint is a security solution designed to protect endpoints across various platforms. It offers AI-powered detection and response, global threat intelligence, and comprehensive protection for devices, including Windows, macOS, Linux, Android, iOS, and IoT. The solution aims to provide robust security and ease of use for businesses of all sizes.
Microsoft Defender for Endpoint Pricing
Microsoft Defender for Endpoint P1: Included with Microsoft 365 E3
Microsoft Defender for Endpoint P2: Included with Microsoft 365 E5
Microsoft Defender for Endpoint Reviews
Microsoft Defender for Endpoint has an overall rating of 4.4 out of 5 stars based on 303 reviews. Users appreciate its comprehensive security features and ease of use. Check out more of our reviews here!
Pros and Cons of Microsoft Defender for Endpoint
Pros:
Multiplatform Support: Protects Windows, macOS, Linux, Android, iOS, and IoT devices, ensuring comprehensive security across diverse environments.
AI-Powered Security: Utilizes artificial intelligence to detect and mitigate cyber threats like ransomware, enhancing the security team's efficiency.
Global Threat Intelligence: Offers a clear view of the cyberattack landscape, providing actionable insights and best practices for prevention.
Cons:
Complexity: Managing and configuring the solution effectively may require significant expertise and resources.
Resource Intensive: The comprehensive security features can potentially impact system performance, especially on older devices.
Cost: Higher price point compared to some other endpoint protection solutions, which might be a concern for small businesses.
7. WatchGuard Endpoint Security

WatchGuard Endpoint Security is a comprehensive solution designed to protect devices from advanced cyber threats. It offers features like Endpoint Detection & Response (EDR), next-gen antivirus, and DNS filtering. With a focus on ease of use and scalability, it aims to provide robust security for businesses of all sizes.
WatchGuard Endpoint Security Pricing
WatchGuard Endpoint Security's pricing is not public. Contact their support for more info.
WatchGuard Endpoint Security Reviews
WatchGuard Endpoint Security has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its ease of use and comprehensive protection. Check out more of our reviews here!
Pros and Cons of WatchGuard Endpoint Security
Pros:
Comprehensive Protection: Integrates next-gen antivirus, EDR, and DNS filtering, ensuring robust defense against diverse cyber threats.
Unified Security Platform: Provides seamless protection for networks, endpoints, Wi-Fi, and identities, enhancing overall security posture.
Cloud-Based Management: Streamlines security administration with a user-friendly interface, centralizing control and reporting.
Cons:
Complexity: The integrated nature of the platform may require a steep learning curve for new users.
Dependency on Cloud: Heavy reliance on cloud-based management might limit use for organizations with strict on-premises requirements.
Potential Cost: The full stack of integrated modules and advanced features might be cost-prohibitive for smaller organizations.
8. Huntress Managed EDR

Huntress Managed EDR is a cybersecurity solution designed to provide comprehensive endpoint detection and response. It focuses on ease of deployment and scalability, making it ideal for small and medium-sized businesses and IT providers. With 24/7 monitoring and expert support, Huntress aims to protect endpoints effectively and efficiently.
Huntress Managed EDR Pricing
Huntress Managed EDR's pricing is not public. Contact their support for more info.
Huntress Managed EDR Reviews
Huntress Managed EDR has an overall rating of 4.9 out of 5 stars based on 663 reviews. Users praise its excellent customer support and ease of use. Check out more of our reviews here!
Pros and Cons of Huntress Managed EDR
Pros:
Customer Support: Users consistently praise Huntress for its responsive and knowledgeable customer support team, ensuring quick resolutions to issues.
Ease of Use: The platform is user-friendly, making it accessible even for those with limited cybersecurity expertise.
Threat Detection: Huntress excels in identifying and mitigating threats, providing robust protection for endpoints.
Cons:
False Positives: Some users report occasional false positives, which can require additional time to investigate and resolve.
Defender Dependence: The platform's effectiveness can be limited by its reliance on Microsoft Defender, potentially impacting non-Windows environments.
Expensive: The cost of the service may be prohibitive for smaller businesses with limited budgets.
9. Kaspersky Endpoint Security Cloud

Kaspersky Endpoint Security Cloud is a cybersecurity solution designed for small to medium-sized businesses. It offers comprehensive protection, ease of use, and seamless deployment. With features like malware protection, ransomware prevention, and cloud security, it aims to provide robust and scalable security for diverse business environments.
Kaspersky Endpoint Security Cloud Pricing
Kaspersky Endpoint Security Cloud's pricing is not public. Contact their support for more info.
Kaspersky Endpoint Security Cloud Reviews
Kaspersky Endpoint Security Cloud has an overall rating of 4.3 out of 5 stars based on 217 reviews. Users appreciate its comprehensive protection but note it can be resource-intensive. Check out more of our reviews here!
Pros and Cons of Kaspersky Endpoint Security Cloud
Pros:
Affordable and Easy to Install: Designed for small to medium-sized businesses, it offers a cost-effective solution that's quick to set up.
Comprehensive Protection: Provides robust defense against malware, ransomware, and other cyber threats, ensuring data security.
Cloud-Based Management: Simplifies security administration with a user-friendly interface, requiring minimal time for management.
Cons:
High Resource Usage: The software can be resource-intensive, potentially slowing down older systems.
Internet Dependence: Requires a stable internet connection for cloud management, which may be a limitation for some users.
Learning Curve: Users unfamiliar with cybersecurity tools may find the initial setup and configuration challenging.
10. NinjaOne

NinjaOne is an IT management solution designed to manage, secure, and support all endpoints. It offers features like endpoint management, remote access, and patch management. With a focus on ease of use and efficiency, NinjaOne aims to provide a secure and scalable solution for businesses of all sizes.
NinjaOne Pricing
NinjaOne's pricing is not public. Contact their support for more info.
NinjaOne Reviews
NinjaOne has an overall rating of 4.8 out of 5 stars based on 1,437 reviews. Users appreciate its ease of use and comprehensive features. Check out more of our reviews here!
Pros and Cons of NinjaOne
Pros:
Comprehensive Endpoint Management: Provides visibility and control over endpoints, supporting various operating systems and devices.
Ease of Use: Quick to implement, easy to learn, and intuitive to use, making it accessible for all skill levels.
Automation: Automates repetitive tasks, freeing up IT teams for more strategic work and improving overall efficiency.
Cons:
Complexity for Small Teams: The extensive features might be overwhelming for smaller IT teams, requiring significant time to master.
Cost: Comprehensive solutions like NinjaOne can be expensive, which might be a consideration for smaller businesses.
Learning Curve: Despite being user-friendly, there might still be a learning curve for new users to fully leverage all features.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern work landscape. Try Twingate for Free today!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions