The Best 10 Alternatives to Microsoft Defender for Endpoint (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024
Microsoft Defender for Endpoint is a security solution designed to protect endpoints across various platforms with advanced detection and response capabilities. While it offers robust features, it might not be the choice for everyone. This article explores how Twingate provides secure access to private resources for distributed workforces under a zero trust networking model.
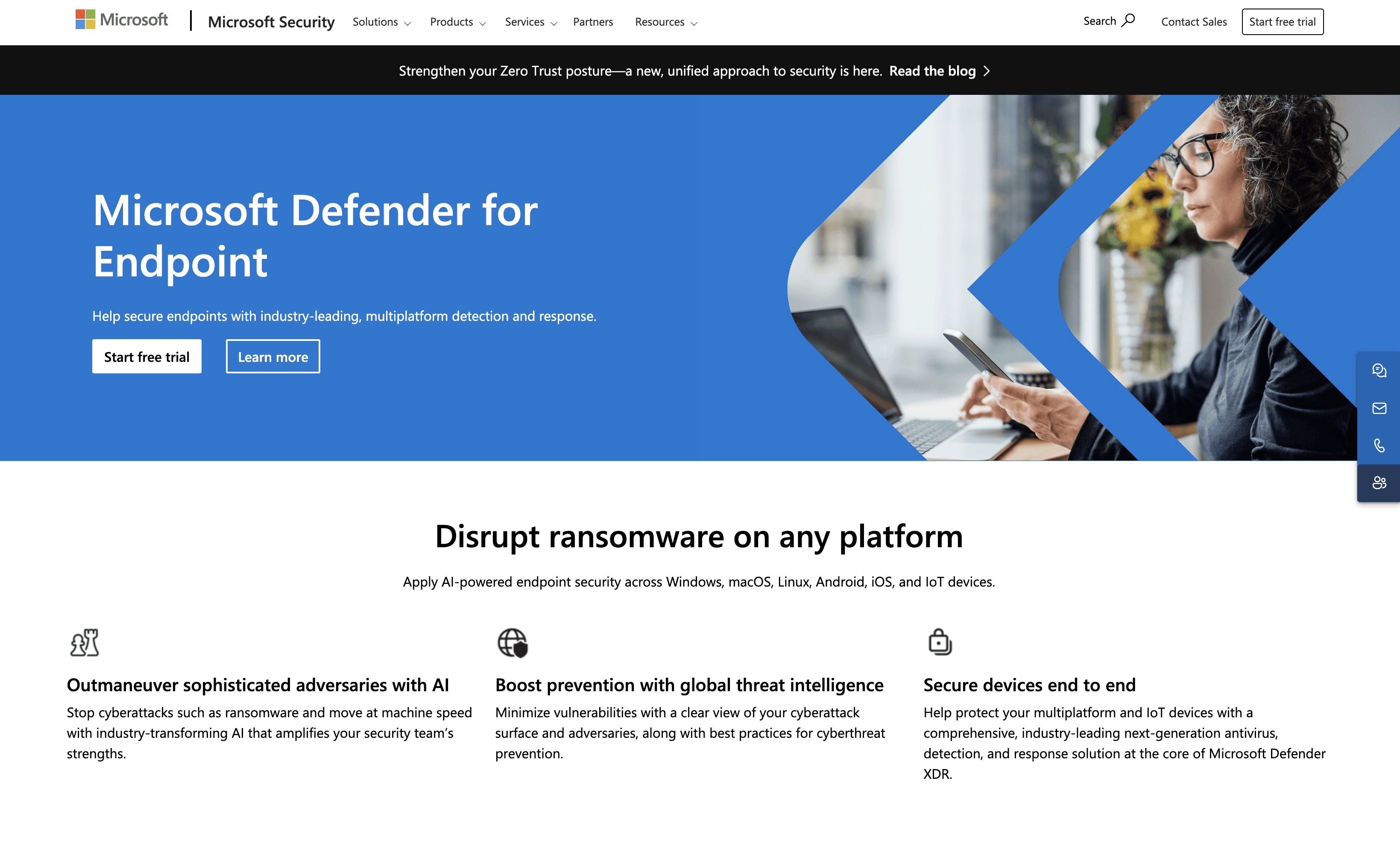
10 Alternatives to Microsoft Defender for Endpoint
1. Bitdefender GravityZone Business Security
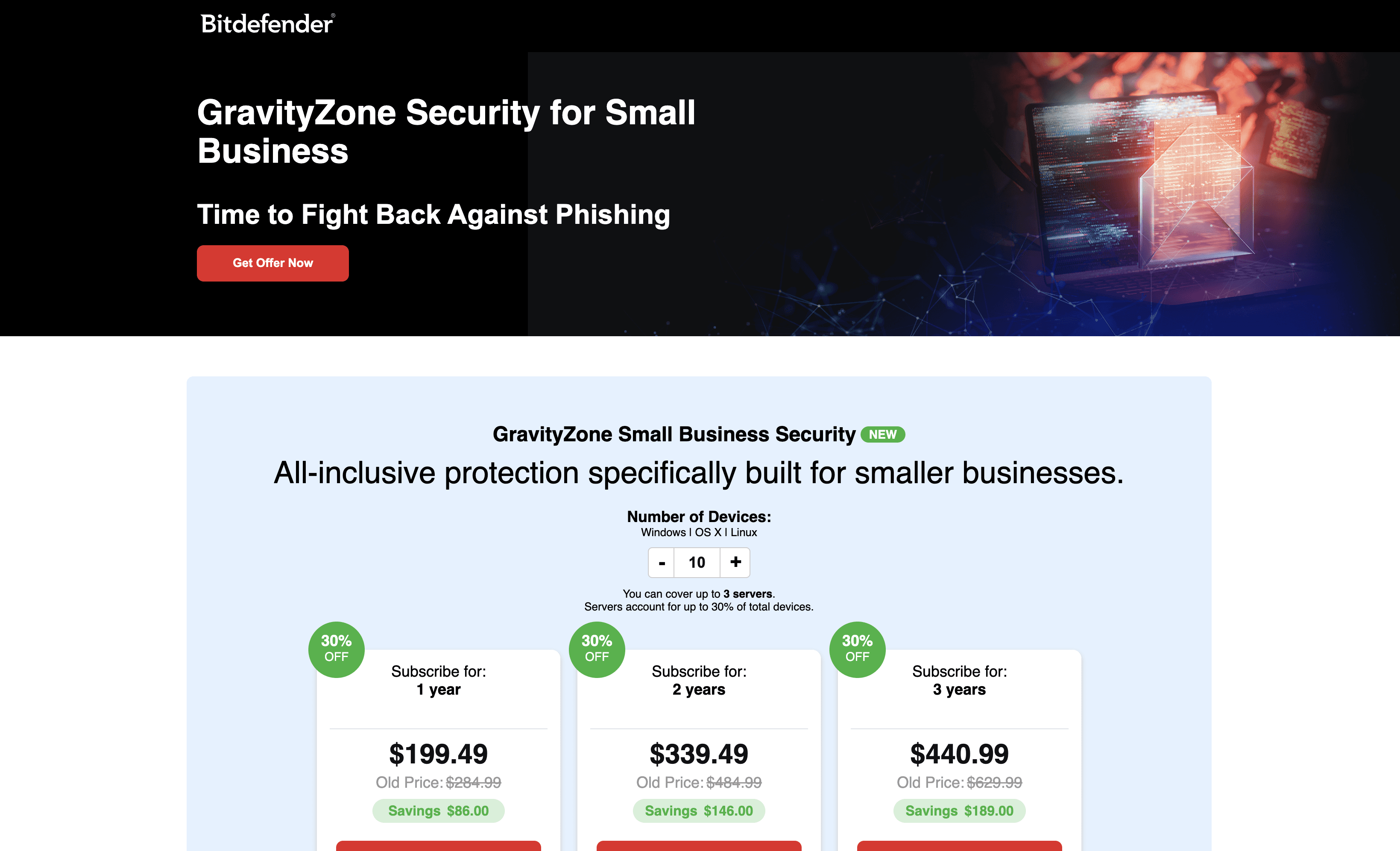
Bitdefender GravityZone Business Security is a comprehensive cybersecurity solution designed for small businesses. It offers robust protection against phishing, ransomware, and other threats, ensuring the safety of your digital assets. With easy deployment and management, it provides scalable security tailored to meet the needs of growing businesses.
Bitdefender GravityZone Business Security Pricing
1 Year Subscription: $199.49
2 Years Subscription: $339.49
3 Years Subscription: $440.99
Bitdefender GravityZone Business Security Reviews
Bitdefender GravityZone Business Security has an overall rating of 4.0 out of 5 stars based on 65 reviews. Users praise its ease of use and effective threat detection. Check out more of our reviews here!
Pros and Cons of Bitdefender GravityZone Business Security
Pros:
Comprehensive protection: Bitdefender GravityZone Business Security offers anti-phishing, fraud prevention, and ransomware protection, ensuring robust defense against various cyber threats.
Ease of use: The solution is designed for simple installation and management, making it accessible even for those without advanced IT security knowledge.
Scalability: As your business grows, Bitdefender GravityZone can scale with it, allowing for add-ons and upgrades to meet evolving security needs.
Cons:
Sales tax not included: The pricing does not account for sales tax, which may result in additional costs for businesses.
Subscription-based: After the trial period, a paid subscription plan is required, which might be a recurring expense for small businesses.
Potential complexity for non-technical users: Despite its user-friendly design, some small businesses without IT staff might find the initial setup and management challenging.
2. Acronis Cyber Protect Cloud
Acronis Cyber Protect Cloud is a comprehensive cyber protection solution designed for Managed Service Providers (MSPs). It integrates data protection, cybersecurity, and endpoint management into a single platform, offering ease of use and scalability. This solution aims to simplify operations while providing robust protection against advanced threats.
Acronis Cyber Protect Cloud Pricing
Acronis Cyber Protect Cloud's pricing is not public. Contact their support for more info.
Acronis Cyber Protect Cloud Reviews
Acronis Cyber Protect Cloud has an overall rating of 4.7 out of 5 stars based on 975 reviews. Users appreciate its ease of use and comprehensive features. Check out more of our reviews here!
Pros and Cons ofAcronis Cyber Protect Cloud
Pros:
Ease of Use: Users find the interface intuitive, making it simple to manage backups and security tasks without extensive training.
Comprehensive Backup Solutions: Acronis Cyber Protect Cloud offers robust backup options, ensuring data safety across physical, virtual, and cloud environments.
Advanced Security Features: The platform integrates AI-based anti-malware and antivirus technologies, providing strong protection against cyber threats.
Cons:
Poor Customer Support: Some users report slow response times and inadequate assistance from the support team.
High Cost: The advanced features come at a premium price, which might be a concern for budget-conscious businesses.
Backup Issues: A few users have experienced problems with backup reliability and performance, impacting their overall experience.
3. WatchGuard Endpoint Security
WatchGuard Endpoint Security is a comprehensive cybersecurity solution designed to protect against advanced threats. It offers next-gen antivirus, Endpoint Detection and Response (EDR), and DNS filtering. With cloud-native security and centralized management through WatchGuard Cloud, it ensures robust protection and ease of use for various devices and operating systems.
WatchGuard Endpoint Security Pricing
WatchGuard Endpoint Security's pricing is not public. Contact their support for more info.
WatchGuard Endpoint Security Reviews
WatchGuard Endpoint Security has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its ease of use and robust protection. Check out more of our reviews here!
Pros and Cons of WatchGuard Endpoint Security
Pros:
Comprehensive Protection: Integrates next-gen antivirus, EDR, and DNS filtering, ensuring robust defense against advanced threats.
Unified Security Platform: Combines network, endpoint, Wi-Fi, and identity protection for holistic security management.
Operational Automation: Centralized administration and reporting through WatchGuard Cloud streamline security operations.
Cons:
Complexity for Small Businesses: Advanced features may overwhelm smaller organizations with limited IT resources.
Dependency on Cloud Services: Reliance on cloud management can be challenging for those with strict data residency needs.
Learning Curve: IT teams may need time to fully utilize the platform’s advanced capabilities.
4. Webroot Business Endpoint Protection
Webroot Business Endpoint Protection is a cloud-based security solution designed to protect against malware, ransomware, and other cyber threats. It offers multi-vector protection, advanced machine learning, and quick deployment, making it an efficient and user-friendly option for businesses of all sizes.
Webroot Business Endpoint Protection Pricing
Webroot Business Endpoint Protection's pricing is not public. Contact their support for more info.
Webroot Business Endpoint Protection Reviews
Webroot Business Endpoint Protection has an overall rating of 4.6 out of 5 stars based on 524 reviews. Users appreciate its ease of use and integration capabilities. Check out more of our reviews here!
Pros and Cons of Webroot Business Endpoint Protection
Pros:
Multi-vector protection: Safeguards against malicious files, scripts, exploits, and URLs, ensuring comprehensive security.
Remote policy management: Enables defining and managing security policies remotely, enhancing administrative efficiency.
Minimal system impact: Designed to have a low footprint, ensuring it doesn't slow down your systems.
Cons:
Agent issues: Some users report problems with the software agent, affecting overall performance.
Compatibility issues: Limited support for certain browsers and operating systems can be restrictive.
Difficult navigation: The interface can be challenging to navigate, especially for new users.
5. Avast Endpoint Protection
Avast Endpoint Protection is a cybersecurity solution designed to safeguard businesses from malware, ransomware, and other threats. It offers multi-layered protection, easy deployment, and centralized management, making it a practical choice for businesses seeking robust and user-friendly security measures.
Avast Endpoint Protection Pricing
Avast Essential Business Security: $148.36 per year
Avast Premium Business Security: $187.00 per year
Avast Ultimate Business Security: $227.08 per year
Avast Endpoint Protection Reviews
Avast Endpoint Protection has an overall rating of 4.4 out of 5 stars based on 101 reviews. Users appreciate its comprehensive protection and user-friendly interface. Check out more of our reviews here!
Pros and Cons of Avast Endpoint Protection
Pros:
Ease of Use: Avast Endpoint Protection is designed for straightforward installation and management, making it accessible even for non-technical users.
Comprehensive Security: Offers multi-layered protection including antivirus, VPN, and cleanup tools, ensuring robust defense against various cyber threats.
Global Trust: Trusted by millions worldwide, reflecting its reliability and effectiveness in providing cybersecurity solutions.
Cons:
Complex Installation: Some users report difficulties during the installation process, which can be a hurdle for those without technical expertise.
Privacy Concerns: The use of cookies and tracking for marketing purposes may raise privacy issues for some users.
Costly Premium Features: Advanced features come at a premium price, which might be a concern for budget-conscious businesses.
6. Crowdstrike
CrowdStrike is a cybersecurity solution designed to prevent breaches using AI-native technology. It offers endpoint security, identity protection, and cloud security, all unified under one platform. With a focus on ease of use and comprehensive protection, CrowdStrike aims to safeguard businesses from modern cyber threats.
Crowdstrike Pricing
Falcon Pro: $99.99/device per year
Falcon Enterprise: $184.99/device per year
Falcon Go (Small Business): $59.99/device per year
Falcon Elite: Contact sales for pricing
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
Crowdstrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users appreciate its advanced threat intelligence and strong architecture. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
AI-Native Platform: CrowdStrike's AI-native platform offers advanced threat detection and response, ensuring proactive cybersecurity measures.
Comprehensive Security Solutions: Provides a wide range of security solutions, including endpoint security, cloud security, and identity protection.
Industry Recognition: Recognized as a leader in industry reports like the Gartner Magic Quadrant, reflecting its reliability and effectiveness.
Cons:
Cost: The advanced features and comprehensive nature of CrowdStrike's solutions can be expensive, posing a barrier for smaller businesses.
Complexity: The wide range of services and solutions might be overwhelming, requiring significant expertise to fully leverage the platform.
False Positives: Some users report false positives, which can lead to unnecessary alerts and potential disruptions.
7. Trend Vision One
Trend Vision One is a cybersecurity solution designed to protect endpoints through every stage of an attack. It offers consolidated security, advanced threat protection, and managed detection and response services. With a focus on operational efficiency, it aims to simplify security management for businesses of all sizes.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its comprehensive threat intelligence and seamless user experience. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Centralized Management: Provides a single solution with a unified view for managing security across endpoints, servers, and cloud workloads.
Enhanced Detection and Response: Includes EDR and XDR capabilities for broader threat detection and faster response.
Operational Efficiency: Streamlines IT security operations with centralized visibility and management.
Cons:
Insufficient Information: Some users report a lack of detailed information, making it hard to fully understand all features.
Confusing Documentation: Documentation can be unclear, leading to difficulties in setup and management.
Integration Issues: Users have experienced problems integrating Trend Vision One with other security tools.
8. F-Secure Elements
F-Secure Elements is a cloud-native security solution designed to protect endpoints with AI-powered threat detection. It offers automated patch management, web browser security, and multi-engine malware protection. With easy deployment and centralized management, it aims to provide comprehensive security for businesses of all sizes.
F-Secure Elements Pricing
WithSecure™ Elements Endpoint Protection for Computers
WithSecure™ Elements Endpoint Protection for Servers
WithSecure™ Elements Mobile Protection
F-Secure Elements's pricing is not public. Contact their support for more info.
F-Secure Elements Reviews
F-Secure Elements has an overall rating of 4.4 out of 5 stars based on 17 reviews. Users appreciate its protection and ease of deployment. Check out more of our reviews here!
Pros and Cons of F-Secure Elements
Pros:
Automated Patch Management: Reduces the risk of attacks by automatically patching vulnerabilities, ensuring systems are always up-to-date.
Web Browser Security: Protects against web-based threats, providing a safer browsing experience for users.
Multi-Engine Malware Protection: Offers robust defense against various types of malware, enhancing overall security.
Cons:
Expensive: Premium features and comprehensive protection might come at a higher price point, which could be a concern for budget-conscious businesses.
Complex Interface: Advanced features may require a learning curve for effective use, potentially overwhelming non-technical users.
Poor Support Services: Some users report inadequate assistance from the support team, leading to unresolved issues.
9. Absolute Secure Endpoint

Absolute Secure Endpoint is a cybersecurity solution designed to protect devices and data with features like application self-healing and ransomware response. It offers visibility, control, and resilience, ensuring robust security for businesses of all sizes. Easy deployment and centralized management make it a practical choice for comprehensive endpoint protection.
Absolute Secure Endpoint Pricing
Absolute Visibility
Absolute Control
Absolute Resilience
Absolute Secure Endpoint's pricing is not public. Contact their support for more info.
Absolute Secure Endpoint Reviews
Absolute Secure Endpoint has an overall rating of 4.6 out of 5 stars based on 307 reviews. Users appreciate its ease of use and reliability. Check out more of our reviews here!
Pros and Cons of Absolute Secure Endpoint
Pros:
Comprehensive Device Tracking: Track hardware, monitor device leasing reports, and track new device activations and connection history.
Software Reporting: Report on installed software by device or population, providing detailed insights into software usage.
Data Collection: Collect data points from the DataExplorer Library and configure custom data points for tailored insights.
Cons:
OS Support Limitations: Some features are limited to specific operating systems, restricting full functionality across all devices.
Feature Availability: Advanced features like Firmware Freeze and Remote Supervisor Password management are only available on eligible devices.
Script Support: Not all scripts in the Absolute Reach library are supported on all operating systems, limiting flexibility.
10. Hexnode UEM
Hexnode UEM is a unified endpoint management solution designed to streamline device management across various platforms. It offers features like remote control, app management, and security policies, ensuring comprehensive protection and ease of use. Hexnode UEM aims to simplify IT operations for businesses of all sizes.
Hexnode UEM Pricing
Hexnode UEM's pricing is not public. Contact their support for more info.
Hexnode UEM Reviews
Hexnode UEM has an overall rating of 4.6 out of 5 stars based on 189 reviews. Users appreciate its ease of use and multi-platform support. Check out more of our reviews here!
Pros and Cons of Hexnode UEM
Pros:
Comprehensive Device Management: Hexnode UEM offers robust management capabilities for various devices, ensuring seamless control and security.
Ease of Use: The platform is user-friendly, making it accessible even for those without extensive technical expertise.
Location Tracking: Provides real-time tracking and logging of device locations, enhancing security and operational efficiency.
Cons:
Missing Features: Some users report the absence of certain desired features, which can limit functionality.
Poor Customer Support: Users have experienced slow response times and inadequate assistance from the support team.
Expensive: The cost of the platform may be high for some businesses, posing a budgetary challenge.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern world of work. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to Microsoft Defender for Endpoint (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024

Microsoft Defender for Endpoint is a security solution designed to protect endpoints across various platforms with advanced detection and response capabilities. While it offers robust features, it might not be the choice for everyone. This article explores how Twingate provides secure access to private resources for distributed workforces under a zero trust networking model.

10 Alternatives to Microsoft Defender for Endpoint
1. Bitdefender GravityZone Business Security

Bitdefender GravityZone Business Security is a comprehensive cybersecurity solution designed for small businesses. It offers robust protection against phishing, ransomware, and other threats, ensuring the safety of your digital assets. With easy deployment and management, it provides scalable security tailored to meet the needs of growing businesses.
Bitdefender GravityZone Business Security Pricing
1 Year Subscription: $199.49
2 Years Subscription: $339.49
3 Years Subscription: $440.99
Bitdefender GravityZone Business Security Reviews
Bitdefender GravityZone Business Security has an overall rating of 4.0 out of 5 stars based on 65 reviews. Users praise its ease of use and effective threat detection. Check out more of our reviews here!
Pros and Cons of Bitdefender GravityZone Business Security
Pros:
Comprehensive protection: Bitdefender GravityZone Business Security offers anti-phishing, fraud prevention, and ransomware protection, ensuring robust defense against various cyber threats.
Ease of use: The solution is designed for simple installation and management, making it accessible even for those without advanced IT security knowledge.
Scalability: As your business grows, Bitdefender GravityZone can scale with it, allowing for add-ons and upgrades to meet evolving security needs.
Cons:
Sales tax not included: The pricing does not account for sales tax, which may result in additional costs for businesses.
Subscription-based: After the trial period, a paid subscription plan is required, which might be a recurring expense for small businesses.
Potential complexity for non-technical users: Despite its user-friendly design, some small businesses without IT staff might find the initial setup and management challenging.
2. Acronis Cyber Protect Cloud

Acronis Cyber Protect Cloud is a comprehensive cyber protection solution designed for Managed Service Providers (MSPs). It integrates data protection, cybersecurity, and endpoint management into a single platform, offering ease of use and scalability. This solution aims to simplify operations while providing robust protection against advanced threats.
Acronis Cyber Protect Cloud Pricing
Acronis Cyber Protect Cloud's pricing is not public. Contact their support for more info.
Acronis Cyber Protect Cloud Reviews
Acronis Cyber Protect Cloud has an overall rating of 4.7 out of 5 stars based on 975 reviews. Users appreciate its ease of use and comprehensive features. Check out more of our reviews here!
Pros and Cons ofAcronis Cyber Protect Cloud
Pros:
Ease of Use: Users find the interface intuitive, making it simple to manage backups and security tasks without extensive training.
Comprehensive Backup Solutions: Acronis Cyber Protect Cloud offers robust backup options, ensuring data safety across physical, virtual, and cloud environments.
Advanced Security Features: The platform integrates AI-based anti-malware and antivirus technologies, providing strong protection against cyber threats.
Cons:
Poor Customer Support: Some users report slow response times and inadequate assistance from the support team.
High Cost: The advanced features come at a premium price, which might be a concern for budget-conscious businesses.
Backup Issues: A few users have experienced problems with backup reliability and performance, impacting their overall experience.
3. WatchGuard Endpoint Security

WatchGuard Endpoint Security is a comprehensive cybersecurity solution designed to protect against advanced threats. It offers next-gen antivirus, Endpoint Detection and Response (EDR), and DNS filtering. With cloud-native security and centralized management through WatchGuard Cloud, it ensures robust protection and ease of use for various devices and operating systems.
WatchGuard Endpoint Security Pricing
WatchGuard Endpoint Security's pricing is not public. Contact their support for more info.
WatchGuard Endpoint Security Reviews
WatchGuard Endpoint Security has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its ease of use and robust protection. Check out more of our reviews here!
Pros and Cons of WatchGuard Endpoint Security
Pros:
Comprehensive Protection: Integrates next-gen antivirus, EDR, and DNS filtering, ensuring robust defense against advanced threats.
Unified Security Platform: Combines network, endpoint, Wi-Fi, and identity protection for holistic security management.
Operational Automation: Centralized administration and reporting through WatchGuard Cloud streamline security operations.
Cons:
Complexity for Small Businesses: Advanced features may overwhelm smaller organizations with limited IT resources.
Dependency on Cloud Services: Reliance on cloud management can be challenging for those with strict data residency needs.
Learning Curve: IT teams may need time to fully utilize the platform’s advanced capabilities.
4. Webroot Business Endpoint Protection

Webroot Business Endpoint Protection is a cloud-based security solution designed to protect against malware, ransomware, and other cyber threats. It offers multi-vector protection, advanced machine learning, and quick deployment, making it an efficient and user-friendly option for businesses of all sizes.
Webroot Business Endpoint Protection Pricing
Webroot Business Endpoint Protection's pricing is not public. Contact their support for more info.
Webroot Business Endpoint Protection Reviews
Webroot Business Endpoint Protection has an overall rating of 4.6 out of 5 stars based on 524 reviews. Users appreciate its ease of use and integration capabilities. Check out more of our reviews here!
Pros and Cons of Webroot Business Endpoint Protection
Pros:
Multi-vector protection: Safeguards against malicious files, scripts, exploits, and URLs, ensuring comprehensive security.
Remote policy management: Enables defining and managing security policies remotely, enhancing administrative efficiency.
Minimal system impact: Designed to have a low footprint, ensuring it doesn't slow down your systems.
Cons:
Agent issues: Some users report problems with the software agent, affecting overall performance.
Compatibility issues: Limited support for certain browsers and operating systems can be restrictive.
Difficult navigation: The interface can be challenging to navigate, especially for new users.
5. Avast Endpoint Protection

Avast Endpoint Protection is a cybersecurity solution designed to safeguard businesses from malware, ransomware, and other threats. It offers multi-layered protection, easy deployment, and centralized management, making it a practical choice for businesses seeking robust and user-friendly security measures.
Avast Endpoint Protection Pricing
Avast Essential Business Security: $148.36 per year
Avast Premium Business Security: $187.00 per year
Avast Ultimate Business Security: $227.08 per year
Avast Endpoint Protection Reviews
Avast Endpoint Protection has an overall rating of 4.4 out of 5 stars based on 101 reviews. Users appreciate its comprehensive protection and user-friendly interface. Check out more of our reviews here!
Pros and Cons of Avast Endpoint Protection
Pros:
Ease of Use: Avast Endpoint Protection is designed for straightforward installation and management, making it accessible even for non-technical users.
Comprehensive Security: Offers multi-layered protection including antivirus, VPN, and cleanup tools, ensuring robust defense against various cyber threats.
Global Trust: Trusted by millions worldwide, reflecting its reliability and effectiveness in providing cybersecurity solutions.
Cons:
Complex Installation: Some users report difficulties during the installation process, which can be a hurdle for those without technical expertise.
Privacy Concerns: The use of cookies and tracking for marketing purposes may raise privacy issues for some users.
Costly Premium Features: Advanced features come at a premium price, which might be a concern for budget-conscious businesses.
6. Crowdstrike

CrowdStrike is a cybersecurity solution designed to prevent breaches using AI-native technology. It offers endpoint security, identity protection, and cloud security, all unified under one platform. With a focus on ease of use and comprehensive protection, CrowdStrike aims to safeguard businesses from modern cyber threats.
Crowdstrike Pricing
Falcon Pro: $99.99/device per year
Falcon Enterprise: $184.99/device per year
Falcon Go (Small Business): $59.99/device per year
Falcon Elite: Contact sales for pricing
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
Crowdstrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users appreciate its advanced threat intelligence and strong architecture. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
AI-Native Platform: CrowdStrike's AI-native platform offers advanced threat detection and response, ensuring proactive cybersecurity measures.
Comprehensive Security Solutions: Provides a wide range of security solutions, including endpoint security, cloud security, and identity protection.
Industry Recognition: Recognized as a leader in industry reports like the Gartner Magic Quadrant, reflecting its reliability and effectiveness.
Cons:
Cost: The advanced features and comprehensive nature of CrowdStrike's solutions can be expensive, posing a barrier for smaller businesses.
Complexity: The wide range of services and solutions might be overwhelming, requiring significant expertise to fully leverage the platform.
False Positives: Some users report false positives, which can lead to unnecessary alerts and potential disruptions.
7. Trend Vision One

Trend Vision One is a cybersecurity solution designed to protect endpoints through every stage of an attack. It offers consolidated security, advanced threat protection, and managed detection and response services. With a focus on operational efficiency, it aims to simplify security management for businesses of all sizes.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its comprehensive threat intelligence and seamless user experience. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Centralized Management: Provides a single solution with a unified view for managing security across endpoints, servers, and cloud workloads.
Enhanced Detection and Response: Includes EDR and XDR capabilities for broader threat detection and faster response.
Operational Efficiency: Streamlines IT security operations with centralized visibility and management.
Cons:
Insufficient Information: Some users report a lack of detailed information, making it hard to fully understand all features.
Confusing Documentation: Documentation can be unclear, leading to difficulties in setup and management.
Integration Issues: Users have experienced problems integrating Trend Vision One with other security tools.
8. F-Secure Elements

F-Secure Elements is a cloud-native security solution designed to protect endpoints with AI-powered threat detection. It offers automated patch management, web browser security, and multi-engine malware protection. With easy deployment and centralized management, it aims to provide comprehensive security for businesses of all sizes.
F-Secure Elements Pricing
WithSecure™ Elements Endpoint Protection for Computers
WithSecure™ Elements Endpoint Protection for Servers
WithSecure™ Elements Mobile Protection
F-Secure Elements's pricing is not public. Contact their support for more info.
F-Secure Elements Reviews
F-Secure Elements has an overall rating of 4.4 out of 5 stars based on 17 reviews. Users appreciate its protection and ease of deployment. Check out more of our reviews here!
Pros and Cons of F-Secure Elements
Pros:
Automated Patch Management: Reduces the risk of attacks by automatically patching vulnerabilities, ensuring systems are always up-to-date.
Web Browser Security: Protects against web-based threats, providing a safer browsing experience for users.
Multi-Engine Malware Protection: Offers robust defense against various types of malware, enhancing overall security.
Cons:
Expensive: Premium features and comprehensive protection might come at a higher price point, which could be a concern for budget-conscious businesses.
Complex Interface: Advanced features may require a learning curve for effective use, potentially overwhelming non-technical users.
Poor Support Services: Some users report inadequate assistance from the support team, leading to unresolved issues.
9. Absolute Secure Endpoint

Absolute Secure Endpoint is a cybersecurity solution designed to protect devices and data with features like application self-healing and ransomware response. It offers visibility, control, and resilience, ensuring robust security for businesses of all sizes. Easy deployment and centralized management make it a practical choice for comprehensive endpoint protection.
Absolute Secure Endpoint Pricing
Absolute Visibility
Absolute Control
Absolute Resilience
Absolute Secure Endpoint's pricing is not public. Contact their support for more info.
Absolute Secure Endpoint Reviews
Absolute Secure Endpoint has an overall rating of 4.6 out of 5 stars based on 307 reviews. Users appreciate its ease of use and reliability. Check out more of our reviews here!
Pros and Cons of Absolute Secure Endpoint
Pros:
Comprehensive Device Tracking: Track hardware, monitor device leasing reports, and track new device activations and connection history.
Software Reporting: Report on installed software by device or population, providing detailed insights into software usage.
Data Collection: Collect data points from the DataExplorer Library and configure custom data points for tailored insights.
Cons:
OS Support Limitations: Some features are limited to specific operating systems, restricting full functionality across all devices.
Feature Availability: Advanced features like Firmware Freeze and Remote Supervisor Password management are only available on eligible devices.
Script Support: Not all scripts in the Absolute Reach library are supported on all operating systems, limiting flexibility.
10. Hexnode UEM

Hexnode UEM is a unified endpoint management solution designed to streamline device management across various platforms. It offers features like remote control, app management, and security policies, ensuring comprehensive protection and ease of use. Hexnode UEM aims to simplify IT operations for businesses of all sizes.
Hexnode UEM Pricing
Hexnode UEM's pricing is not public. Contact their support for more info.
Hexnode UEM Reviews
Hexnode UEM has an overall rating of 4.6 out of 5 stars based on 189 reviews. Users appreciate its ease of use and multi-platform support. Check out more of our reviews here!
Pros and Cons of Hexnode UEM
Pros:
Comprehensive Device Management: Hexnode UEM offers robust management capabilities for various devices, ensuring seamless control and security.
Ease of Use: The platform is user-friendly, making it accessible even for those without extensive technical expertise.
Location Tracking: Provides real-time tracking and logging of device locations, enhancing security and operational efficiency.
Cons:
Missing Features: Some users report the absence of certain desired features, which can limit functionality.
Poor Customer Support: Users have experienced slow response times and inadequate assistance from the support team.
Expensive: The cost of the platform may be high for some businesses, posing a budgetary challenge.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern world of work. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to Microsoft Defender for Endpoint (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024

Microsoft Defender for Endpoint is a security solution designed to protect endpoints across various platforms with advanced detection and response capabilities. While it offers robust features, it might not be the choice for everyone. This article explores how Twingate provides secure access to private resources for distributed workforces under a zero trust networking model.

10 Alternatives to Microsoft Defender for Endpoint
1. Bitdefender GravityZone Business Security

Bitdefender GravityZone Business Security is a comprehensive cybersecurity solution designed for small businesses. It offers robust protection against phishing, ransomware, and other threats, ensuring the safety of your digital assets. With easy deployment and management, it provides scalable security tailored to meet the needs of growing businesses.
Bitdefender GravityZone Business Security Pricing
1 Year Subscription: $199.49
2 Years Subscription: $339.49
3 Years Subscription: $440.99
Bitdefender GravityZone Business Security Reviews
Bitdefender GravityZone Business Security has an overall rating of 4.0 out of 5 stars based on 65 reviews. Users praise its ease of use and effective threat detection. Check out more of our reviews here!
Pros and Cons of Bitdefender GravityZone Business Security
Pros:
Comprehensive protection: Bitdefender GravityZone Business Security offers anti-phishing, fraud prevention, and ransomware protection, ensuring robust defense against various cyber threats.
Ease of use: The solution is designed for simple installation and management, making it accessible even for those without advanced IT security knowledge.
Scalability: As your business grows, Bitdefender GravityZone can scale with it, allowing for add-ons and upgrades to meet evolving security needs.
Cons:
Sales tax not included: The pricing does not account for sales tax, which may result in additional costs for businesses.
Subscription-based: After the trial period, a paid subscription plan is required, which might be a recurring expense for small businesses.
Potential complexity for non-technical users: Despite its user-friendly design, some small businesses without IT staff might find the initial setup and management challenging.
2. Acronis Cyber Protect Cloud

Acronis Cyber Protect Cloud is a comprehensive cyber protection solution designed for Managed Service Providers (MSPs). It integrates data protection, cybersecurity, and endpoint management into a single platform, offering ease of use and scalability. This solution aims to simplify operations while providing robust protection against advanced threats.
Acronis Cyber Protect Cloud Pricing
Acronis Cyber Protect Cloud's pricing is not public. Contact their support for more info.
Acronis Cyber Protect Cloud Reviews
Acronis Cyber Protect Cloud has an overall rating of 4.7 out of 5 stars based on 975 reviews. Users appreciate its ease of use and comprehensive features. Check out more of our reviews here!
Pros and Cons ofAcronis Cyber Protect Cloud
Pros:
Ease of Use: Users find the interface intuitive, making it simple to manage backups and security tasks without extensive training.
Comprehensive Backup Solutions: Acronis Cyber Protect Cloud offers robust backup options, ensuring data safety across physical, virtual, and cloud environments.
Advanced Security Features: The platform integrates AI-based anti-malware and antivirus technologies, providing strong protection against cyber threats.
Cons:
Poor Customer Support: Some users report slow response times and inadequate assistance from the support team.
High Cost: The advanced features come at a premium price, which might be a concern for budget-conscious businesses.
Backup Issues: A few users have experienced problems with backup reliability and performance, impacting their overall experience.
3. WatchGuard Endpoint Security

WatchGuard Endpoint Security is a comprehensive cybersecurity solution designed to protect against advanced threats. It offers next-gen antivirus, Endpoint Detection and Response (EDR), and DNS filtering. With cloud-native security and centralized management through WatchGuard Cloud, it ensures robust protection and ease of use for various devices and operating systems.
WatchGuard Endpoint Security Pricing
WatchGuard Endpoint Security's pricing is not public. Contact their support for more info.
WatchGuard Endpoint Security Reviews
WatchGuard Endpoint Security has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its ease of use and robust protection. Check out more of our reviews here!
Pros and Cons of WatchGuard Endpoint Security
Pros:
Comprehensive Protection: Integrates next-gen antivirus, EDR, and DNS filtering, ensuring robust defense against advanced threats.
Unified Security Platform: Combines network, endpoint, Wi-Fi, and identity protection for holistic security management.
Operational Automation: Centralized administration and reporting through WatchGuard Cloud streamline security operations.
Cons:
Complexity for Small Businesses: Advanced features may overwhelm smaller organizations with limited IT resources.
Dependency on Cloud Services: Reliance on cloud management can be challenging for those with strict data residency needs.
Learning Curve: IT teams may need time to fully utilize the platform’s advanced capabilities.
4. Webroot Business Endpoint Protection

Webroot Business Endpoint Protection is a cloud-based security solution designed to protect against malware, ransomware, and other cyber threats. It offers multi-vector protection, advanced machine learning, and quick deployment, making it an efficient and user-friendly option for businesses of all sizes.
Webroot Business Endpoint Protection Pricing
Webroot Business Endpoint Protection's pricing is not public. Contact their support for more info.
Webroot Business Endpoint Protection Reviews
Webroot Business Endpoint Protection has an overall rating of 4.6 out of 5 stars based on 524 reviews. Users appreciate its ease of use and integration capabilities. Check out more of our reviews here!
Pros and Cons of Webroot Business Endpoint Protection
Pros:
Multi-vector protection: Safeguards against malicious files, scripts, exploits, and URLs, ensuring comprehensive security.
Remote policy management: Enables defining and managing security policies remotely, enhancing administrative efficiency.
Minimal system impact: Designed to have a low footprint, ensuring it doesn't slow down your systems.
Cons:
Agent issues: Some users report problems with the software agent, affecting overall performance.
Compatibility issues: Limited support for certain browsers and operating systems can be restrictive.
Difficult navigation: The interface can be challenging to navigate, especially for new users.
5. Avast Endpoint Protection

Avast Endpoint Protection is a cybersecurity solution designed to safeguard businesses from malware, ransomware, and other threats. It offers multi-layered protection, easy deployment, and centralized management, making it a practical choice for businesses seeking robust and user-friendly security measures.
Avast Endpoint Protection Pricing
Avast Essential Business Security: $148.36 per year
Avast Premium Business Security: $187.00 per year
Avast Ultimate Business Security: $227.08 per year
Avast Endpoint Protection Reviews
Avast Endpoint Protection has an overall rating of 4.4 out of 5 stars based on 101 reviews. Users appreciate its comprehensive protection and user-friendly interface. Check out more of our reviews here!
Pros and Cons of Avast Endpoint Protection
Pros:
Ease of Use: Avast Endpoint Protection is designed for straightforward installation and management, making it accessible even for non-technical users.
Comprehensive Security: Offers multi-layered protection including antivirus, VPN, and cleanup tools, ensuring robust defense against various cyber threats.
Global Trust: Trusted by millions worldwide, reflecting its reliability and effectiveness in providing cybersecurity solutions.
Cons:
Complex Installation: Some users report difficulties during the installation process, which can be a hurdle for those without technical expertise.
Privacy Concerns: The use of cookies and tracking for marketing purposes may raise privacy issues for some users.
Costly Premium Features: Advanced features come at a premium price, which might be a concern for budget-conscious businesses.
6. Crowdstrike

CrowdStrike is a cybersecurity solution designed to prevent breaches using AI-native technology. It offers endpoint security, identity protection, and cloud security, all unified under one platform. With a focus on ease of use and comprehensive protection, CrowdStrike aims to safeguard businesses from modern cyber threats.
Crowdstrike Pricing
Falcon Pro: $99.99/device per year
Falcon Enterprise: $184.99/device per year
Falcon Go (Small Business): $59.99/device per year
Falcon Elite: Contact sales for pricing
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
Crowdstrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users appreciate its advanced threat intelligence and strong architecture. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
AI-Native Platform: CrowdStrike's AI-native platform offers advanced threat detection and response, ensuring proactive cybersecurity measures.
Comprehensive Security Solutions: Provides a wide range of security solutions, including endpoint security, cloud security, and identity protection.
Industry Recognition: Recognized as a leader in industry reports like the Gartner Magic Quadrant, reflecting its reliability and effectiveness.
Cons:
Cost: The advanced features and comprehensive nature of CrowdStrike's solutions can be expensive, posing a barrier for smaller businesses.
Complexity: The wide range of services and solutions might be overwhelming, requiring significant expertise to fully leverage the platform.
False Positives: Some users report false positives, which can lead to unnecessary alerts and potential disruptions.
7. Trend Vision One

Trend Vision One is a cybersecurity solution designed to protect endpoints through every stage of an attack. It offers consolidated security, advanced threat protection, and managed detection and response services. With a focus on operational efficiency, it aims to simplify security management for businesses of all sizes.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its comprehensive threat intelligence and seamless user experience. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Centralized Management: Provides a single solution with a unified view for managing security across endpoints, servers, and cloud workloads.
Enhanced Detection and Response: Includes EDR and XDR capabilities for broader threat detection and faster response.
Operational Efficiency: Streamlines IT security operations with centralized visibility and management.
Cons:
Insufficient Information: Some users report a lack of detailed information, making it hard to fully understand all features.
Confusing Documentation: Documentation can be unclear, leading to difficulties in setup and management.
Integration Issues: Users have experienced problems integrating Trend Vision One with other security tools.
8. F-Secure Elements

F-Secure Elements is a cloud-native security solution designed to protect endpoints with AI-powered threat detection. It offers automated patch management, web browser security, and multi-engine malware protection. With easy deployment and centralized management, it aims to provide comprehensive security for businesses of all sizes.
F-Secure Elements Pricing
WithSecure™ Elements Endpoint Protection for Computers
WithSecure™ Elements Endpoint Protection for Servers
WithSecure™ Elements Mobile Protection
F-Secure Elements's pricing is not public. Contact their support for more info.
F-Secure Elements Reviews
F-Secure Elements has an overall rating of 4.4 out of 5 stars based on 17 reviews. Users appreciate its protection and ease of deployment. Check out more of our reviews here!
Pros and Cons of F-Secure Elements
Pros:
Automated Patch Management: Reduces the risk of attacks by automatically patching vulnerabilities, ensuring systems are always up-to-date.
Web Browser Security: Protects against web-based threats, providing a safer browsing experience for users.
Multi-Engine Malware Protection: Offers robust defense against various types of malware, enhancing overall security.
Cons:
Expensive: Premium features and comprehensive protection might come at a higher price point, which could be a concern for budget-conscious businesses.
Complex Interface: Advanced features may require a learning curve for effective use, potentially overwhelming non-technical users.
Poor Support Services: Some users report inadequate assistance from the support team, leading to unresolved issues.
9. Absolute Secure Endpoint

Absolute Secure Endpoint is a cybersecurity solution designed to protect devices and data with features like application self-healing and ransomware response. It offers visibility, control, and resilience, ensuring robust security for businesses of all sizes. Easy deployment and centralized management make it a practical choice for comprehensive endpoint protection.
Absolute Secure Endpoint Pricing
Absolute Visibility
Absolute Control
Absolute Resilience
Absolute Secure Endpoint's pricing is not public. Contact their support for more info.
Absolute Secure Endpoint Reviews
Absolute Secure Endpoint has an overall rating of 4.6 out of 5 stars based on 307 reviews. Users appreciate its ease of use and reliability. Check out more of our reviews here!
Pros and Cons of Absolute Secure Endpoint
Pros:
Comprehensive Device Tracking: Track hardware, monitor device leasing reports, and track new device activations and connection history.
Software Reporting: Report on installed software by device or population, providing detailed insights into software usage.
Data Collection: Collect data points from the DataExplorer Library and configure custom data points for tailored insights.
Cons:
OS Support Limitations: Some features are limited to specific operating systems, restricting full functionality across all devices.
Feature Availability: Advanced features like Firmware Freeze and Remote Supervisor Password management are only available on eligible devices.
Script Support: Not all scripts in the Absolute Reach library are supported on all operating systems, limiting flexibility.
10. Hexnode UEM

Hexnode UEM is a unified endpoint management solution designed to streamline device management across various platforms. It offers features like remote control, app management, and security policies, ensuring comprehensive protection and ease of use. Hexnode UEM aims to simplify IT operations for businesses of all sizes.
Hexnode UEM Pricing
Hexnode UEM's pricing is not public. Contact their support for more info.
Hexnode UEM Reviews
Hexnode UEM has an overall rating of 4.6 out of 5 stars based on 189 reviews. Users appreciate its ease of use and multi-platform support. Check out more of our reviews here!
Pros and Cons of Hexnode UEM
Pros:
Comprehensive Device Management: Hexnode UEM offers robust management capabilities for various devices, ensuring seamless control and security.
Ease of Use: The platform is user-friendly, making it accessible even for those without extensive technical expertise.
Location Tracking: Provides real-time tracking and logging of device locations, enhancing security and operational efficiency.
Cons:
Missing Features: Some users report the absence of certain desired features, which can limit functionality.
Poor Customer Support: Users have experienced slow response times and inadequate assistance from the support team.
Expensive: The cost of the platform may be high for some businesses, posing a budgetary challenge.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern world of work. Try Twingate for Free today!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions