The Best 10 Alternatives to NinjaOne (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024
NinjaOne provides unified IT management solutions that help IT teams manage, secure, and support endpoints. Their platform includes features like endpoint management, remote control, RMM, backup, patch management, and more. While NinjaOne offers robust solutions, it might not be the choice for everyone. This article explores the benefits and considerations of using NinjaOne.

10 Alternatives to NinjaOne
1. Symantec
Symantec is a comprehensive cybersecurity solution designed to protect large enterprises. It offers data-centric hybrid security, compliance, remote work security, and threat protection. With a focus on innovation and AI, Symantec aims to provide robust security measures that adapt to organizational changes and integrate seamlessly with existing infrastructures.
Symantec Pricing
Symantec's pricing is not public. Contact their support for more info.
Symantec Reviews
Symantec has an overall rating of 4.3 out of 5 stars based on 37 reviews. Users appreciate its advanced security features and ease of use. Check out more of our reviews here!
Pros and Cons of Symantec
Pros:
Symantec Enterprise Cloud offers comprehensive security, covering devices, private data centers, and the cloud, ensuring robust protection across all platforms.
It ensures consistent compliance, making it easier for enterprises to manage and apply compliance controls across their entire infrastructure.
With its secure remote work capabilities, Symantec protects critical enterprise assets regardless of their location, enhancing security for distributed workforces.
Cons:
The advanced features and comprehensive nature of Symantec may be too complex or costly for smaller organizations, making it more suitable for large enterprises.
While Symantec supports migration between on-premises and cloud environments, the process can still pose challenges for some organizations.
Heavy reliance on AI and automation might raise concerns about the accuracy and reliability of threat detection and response in certain scenarios.
2. Huntress Managed EDR
Huntress Managed EDR is a cybersecurity solution designed to provide full visibility, detection, and response for endpoints. It defends against attacks in real-time, ensuring comprehensive protection. With easy deployment and a user-friendly interface, it’s ideal for small and medium-sized businesses looking to enhance their security posture.
Huntress Managed EDR Pricing
Huntress Managed EDR's pricing is not public. Contact their support for more info.
Huntress Managed EDR Reviews
Huntress Managed EDR has an overall rating of 4.9 out of 5 stars based on 663 reviews. Users appreciate its ease of use and effective threat detection. Check out more of our reviews here!
Pros and Cons ofHuntress Managed EDR
Pros:
Full Visibility: Huntress Managed EDR provides comprehensive visibility, detection, and response for endpoints, ensuring no threat goes unnoticed.
Ease of Use: Users appreciate its intuitive interface, making it accessible even for those not deeply familiar with cybersecurity software.
24/7 Support: Supported by expert analysts in a 24/7 Security Operations Center (SOC), ensuring continuous protection and quick response to threats.
Cons:
Cost Concerns: The service can be expensive, which might be a barrier for budget-conscious small and medium-sized businesses.
False Positives: Some users report occasional false positives, which can lead to unnecessary alerts and potential disruptions.
Defender Dependence: The platform's reliance on Microsoft Defender might limit its effectiveness in environments where Defender is not the primary security tool.
3. Cylance
Cylance is an AI-driven cybersecurity solution designed to protect against advanced threats. It offers endpoint security, managed detection and response, and zero trust network access. With a focus on proactive threat prevention and low resource usage, Cylance aims to provide robust protection for businesses of all sizes.
Cylance Pricing
Cylance's pricing is not public. Contact their support for more info.
Cylance Reviews
Cylance has an overall rating of 4.3 out of 5 stars based on 57 reviews. Users appreciate its AI-driven approach and ease of use. Check out more of our reviews here!
Pros and Cons of Cylance
Pros:
AI-Driven Security: Cylance's AI-driven solutions deliver high efficacy with minimal CPU usage, even offline, ensuring robust protection without draining system resources.
Broad, Integrated Controls: The platform offers comprehensive security across network, endpoint, and cloud, effectively stopping more malware and providing a resilient defense.
Operational Excellence: Cylance prioritizes best practices, ensuring updates are thoroughly vetted to minimize the risk of large-scale outages, maintaining system stability.
Cons:
Initial Training Period: The product requires a training period to adapt to the environment, which might demand initial effort and time from the IT team.
Dependency on AI: Heavy reliance on AI could be a concern for organizations preferring more human oversight or those less trusting of automated systems.
Complexity for Small Organizations: The extensive controls might be overwhelming for smaller organizations with limited IT resources, complicating deployment and management.
4. Threatlocker

ThreatLocker is a cybersecurity solution focused on Zero Trust endpoint protection. It offers features like allowlisting, Ringfencing™, and network control to secure applications and data. With easy deployment and centralized management, ThreatLocker aims to provide robust security for businesses of all sizes.
Threatlocker Pricing
Threatlocker's pricing is not public. Contact their support for more info.
Threatlocker Reviews
ThreatLocker has an overall rating of 4.8 out of 5 stars based on 162 reviews. Users praise its strong security features and excellent support. Check out more of our reviews here!
Pros and Cons of Threatlocker
Pros:
Zero Trust Security: ThreatLocker blocks all applications and scripts except those explicitly allowed, ensuring robust endpoint protection.
Comprehensive Protection: Defends against ransomware, zero-day vulnerabilities, and other malicious software, providing a secure environment.
Unified Audit: Centralized audit logs offer a clear view of all activities, simplifying compliance and monitoring.
Cons:
Complexity: The extensive features and configurations can be overwhelming for smaller organizations or those without dedicated IT staff.
Cost: Enterprise-level security solutions like ThreatLocker can be expensive, posing a barrier for small to medium-sized businesses.
Learning Curve: Users report a steep learning curve, requiring significant time and effort to master the platform.
5. Crowdstrike
CrowdStrike is a cybersecurity solution that leverages AI to prevent breaches. It offers endpoint security, threat intelligence, and cloud security, aiming to provide comprehensive protection for businesses of all sizes. With easy deployment and robust features, CrowdStrike ensures a secure environment for modern enterprises.
Crowdstrike Pricing
Falcon Pro: $99.99/device annually
Falcon Enterprise: $184.99/device annually
Falcon Go: $59.99/device annually
Falcon Elite: Contact sales for pricing
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
CrowdStrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users praise its advanced threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
AI-native Platform: CrowdStrike leverages artificial intelligence to enhance cybersecurity, providing advanced threat detection and response capabilities.
Comprehensive Solutions: Offers endpoint security, exposure management, identity protection, and more, ensuring robust protection across various vectors.
Industry Recognition: Recognized as a leader in cybersecurity by Gartner and Forrester, validating its effectiveness and reliability.
Cons:
Complexity for Small Businesses: The platform's extensive features can be overwhelming for smaller organizations with limited IT resources.
Cost: Advanced cybersecurity solutions like CrowdStrike can be expensive, posing a barrier for budget-conscious businesses.
False Positives: Some users report occasional false positives, which can lead to unnecessary alerts and potential disruptions.
6. Vipre EDR

Vipre EDR is a cybersecurity solution designed to provide comprehensive endpoint protection. It features easy installation, ransomware prevention, AI-powered threat investigation, and mobile accessibility. Vipre aims to offer robust security for businesses of all sizes, ensuring effective threat detection and response with minimal complexity.
Vipre EDR Pricing
Vipre EDR's pricing is not public. Contact their support for more info.
Vipre EDR Reviews
Vipre EDR has an overall rating of 4.5 out of 5 stars based on 50 reviews. Users appreciate its robust threat detection and ease of use. Check out more of our reviews here!
Pros and Cons of Vipre EDR
Pros:
Easy Installation: VIPRE EDR combines advanced functionality with simple installation, making it accessible for businesses of all sizes.
Ransomware Prevention: Utilizes real-time behavior monitoring and AI to detect, prevent, and roll back ransomware attacks effectively.
Comprehensive Threat View: Provides a centralized location for viewing, investigating, and addressing threats, ensuring no threat goes unnoticed.
Cons:
Limited Reviews: There are not enough user reviews to provide comprehensive buying insights, which may deter potential customers.
Profile Limitations: The claimed profile on review sites has limited features, potentially affecting the visibility and credibility of the product.
Security Information: The seller has not added detailed security information, leaving users to request this crucial data independently.
7. Avast Endpoint Protection
Avast Endpoint Protection is a cybersecurity solution designed to safeguard businesses from cyber threats. It offers comprehensive endpoint security, easy deployment, and centralized management. With features like antivirus, firewall, and behavior analysis, Avast aims to provide robust protection for businesses of all sizes, ensuring a secure and efficient environment.
Avast Endpoint Protection Pricing
Avast Essential Business Security: $148.36/year
Avast Premium Business Security: $187.00/year
Avast Ultimate Business Security: $227.08/year
Avast Endpoint Protection Reviews
Avast Endpoint Protection has an overall rating of 4.4 out of 5 stars based on 101 reviews. Users appreciate its rich security features and user-friendly controls. Check out more of our reviews here!
Pros and Cons of Avast Endpoint Protection
Pros:
Ease of Use: Avast Endpoint Protection is user-friendly, making it accessible even for those not well-versed in cybersecurity.
Comprehensive Protection: Offers a suite of tools including antivirus, VPN, and cleanup utilities, ensuring robust security.
Global Trust: Trusted by millions worldwide, reflecting its reliability and effectiveness in protecting against threats.
Cons:
Privacy Concerns: Past issues with data privacy and selling user data have raised concerns among users.
Pop-up Ads: The free version includes pop-up ads, which can be intrusive and prompt users to upgrade.
Resource Usage: While generally lightweight, some users report performance impacts on older devices.
8. WatchGuard Panda Adaptive Defense 360
WatchGuard Panda Adaptive Defense 360 is a cybersecurity solution designed to provide advanced endpoint protection. It combines Endpoint Protection (EPP) and Endpoint Detection and Response (EDR) capabilities, offering continuous monitoring, threat hunting, and automated response. Ideal for businesses of all sizes, it ensures robust security with minimal complexity.
WatchGuard Panda Adaptive Defense 360 Pricing
WatchGuard Panda Adaptive Defense 360's pricing is not public. Contact their support for more info.
WatchGuard Panda Adaptive Defense 360 Reviews
WatchGuard Panda Adaptive Defense 360 has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its robust protection and ease of use. Check out more of our reviews here!
Pros and Cons of WatchGuard Panda Adaptive Defense 360
Pros:
Zero-Trust Application Service: Ensures 100% classification of processes, blocking any suspicious activity, enhancing overall security.
Automated Detection and Response: Reduces detection, response, and investigation time, streamlining threat management.
Forensic Information: Provides detailed forensic data to investigate attacks and mitigate effects, aiding in comprehensive threat analysis.
Cons:
Complexity: The advanced features and comprehensive protection might require significant expertise to manage effectively.
Cost: Advanced security solutions like AD360 can be expensive, which might be a consideration for smaller organizations.
Dependency on Cloud: As a cloud-delivered solution, it may require reliable internet connectivity and could be less effective in environments with limited or no internet access.
9. Carbon Black
Carbon Black is a cybersecurity solution designed to protect endpoints from advanced threats. It offers real-time threat detection, response, and prevention, ensuring robust security for businesses of all sizes. With easy deployment and AI-driven insights, Carbon Black aims to provide comprehensive protection with minimal complexity.
Carbon Black Pricing
Carbon Black's pricing is not public. Contact their support for more info.
Carbon Black Reviews
Carbon Black has an overall rating of 4.3 out of 5 stars based on 37 reviews. Users appreciate its ease of installation and robust protection. Check out more of our reviews here!
Pros and Cons of Carbon Black
Pros:
Robust Protection: Carbon Black offers strong defense against various cyber threats, ensuring comprehensive security for endpoints.
Easy Installation: Users find the installation process straightforward, making it accessible even for those with limited technical expertise.
Effective Monitoring: The platform provides excellent monitoring capabilities, allowing for real-time threat detection and response.
Cons:
Agent Removal Issues: Some users report difficulties in removing the agent, which can complicate system management.
Complex Installation: Despite its ease for some, others find the installation process complex and time-consuming.
Delay Issues: There are mentions of delays in certain functionalities, which can affect overall performance.
10. Trend Vision One
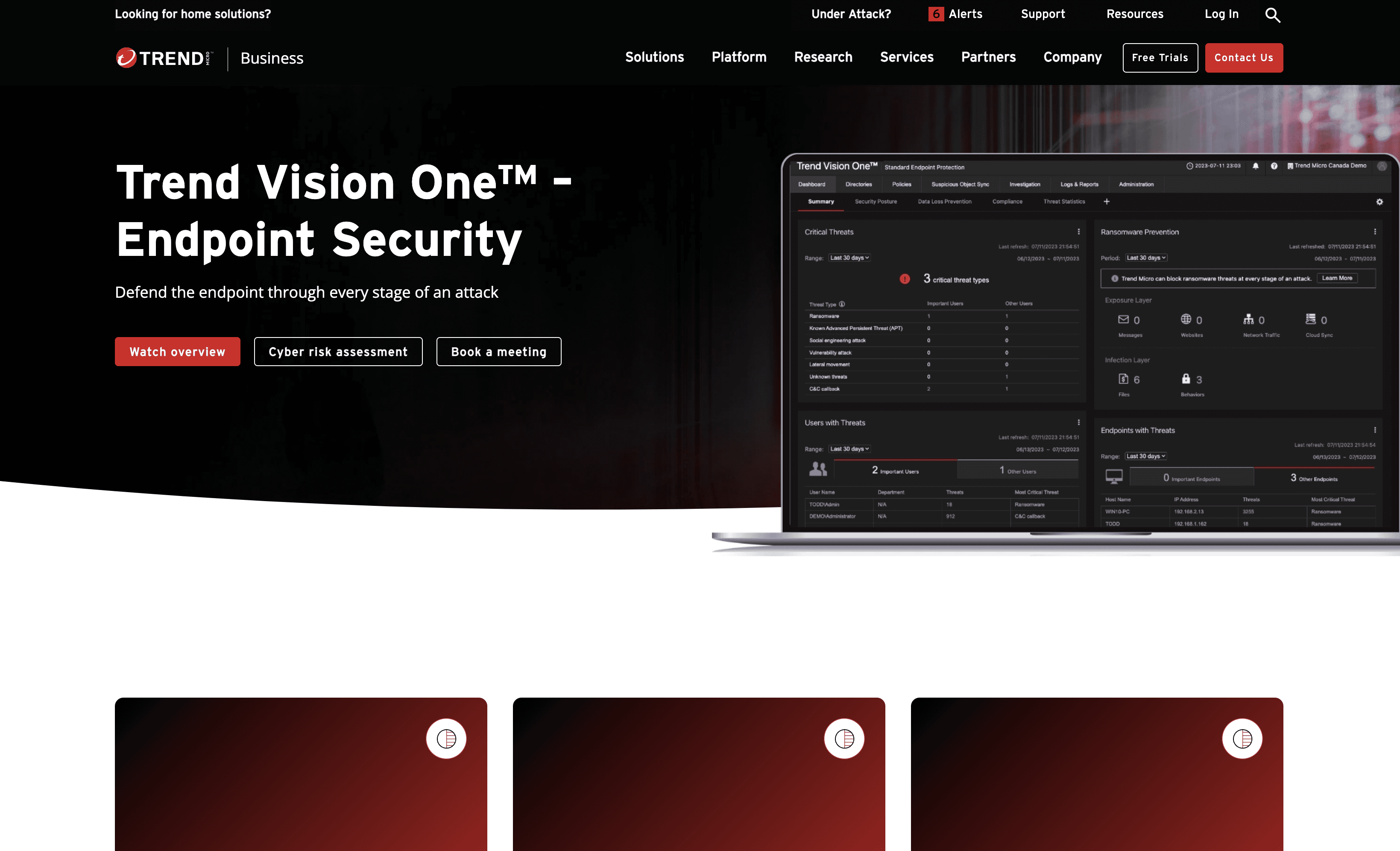
Trend Vision One is an endpoint security solution designed to defend against cyber threats at every stage of an attack. It offers centralized management, advanced threat protection, and streamlined IT operations. With features like EDR and XDR, Trend Vision One aims to provide comprehensive security for businesses of all sizes.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its unified platform and comprehensive threat intelligence. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Consolidated Security: Provides a unified view for endpoint, server, and workload security, simplifying management and enhancing visibility.
Enhanced Detection and Response: Advanced EDR and XDR capabilities ensure effective threat detection, investigation, and response.
Operational Efficiency: Centralized management streamlines IT operations, covering inventory, detections, risk mitigation, policies, and licenses.
Cons:
Complexity: The comprehensive nature of the solution might be challenging to implement and manage for smaller organizations.
Cost: Advanced features and managed services can be expensive, posing a barrier for budget-conscious businesses.
Learning Curve: Users may require training to fully utilize the platform's advanced capabilities, impacting initial deployment.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern work landscape. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to NinjaOne (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024

NinjaOne provides unified IT management solutions that help IT teams manage, secure, and support endpoints. Their platform includes features like endpoint management, remote control, RMM, backup, patch management, and more. While NinjaOne offers robust solutions, it might not be the choice for everyone. This article explores the benefits and considerations of using NinjaOne.

10 Alternatives to NinjaOne
1. Symantec

Symantec is a comprehensive cybersecurity solution designed to protect large enterprises. It offers data-centric hybrid security, compliance, remote work security, and threat protection. With a focus on innovation and AI, Symantec aims to provide robust security measures that adapt to organizational changes and integrate seamlessly with existing infrastructures.
Symantec Pricing
Symantec's pricing is not public. Contact their support for more info.
Symantec Reviews
Symantec has an overall rating of 4.3 out of 5 stars based on 37 reviews. Users appreciate its advanced security features and ease of use. Check out more of our reviews here!
Pros and Cons of Symantec
Pros:
Symantec Enterprise Cloud offers comprehensive security, covering devices, private data centers, and the cloud, ensuring robust protection across all platforms.
It ensures consistent compliance, making it easier for enterprises to manage and apply compliance controls across their entire infrastructure.
With its secure remote work capabilities, Symantec protects critical enterprise assets regardless of their location, enhancing security for distributed workforces.
Cons:
The advanced features and comprehensive nature of Symantec may be too complex or costly for smaller organizations, making it more suitable for large enterprises.
While Symantec supports migration between on-premises and cloud environments, the process can still pose challenges for some organizations.
Heavy reliance on AI and automation might raise concerns about the accuracy and reliability of threat detection and response in certain scenarios.
2. Huntress Managed EDR

Huntress Managed EDR is a cybersecurity solution designed to provide full visibility, detection, and response for endpoints. It defends against attacks in real-time, ensuring comprehensive protection. With easy deployment and a user-friendly interface, it’s ideal for small and medium-sized businesses looking to enhance their security posture.
Huntress Managed EDR Pricing
Huntress Managed EDR's pricing is not public. Contact their support for more info.
Huntress Managed EDR Reviews
Huntress Managed EDR has an overall rating of 4.9 out of 5 stars based on 663 reviews. Users appreciate its ease of use and effective threat detection. Check out more of our reviews here!
Pros and Cons ofHuntress Managed EDR
Pros:
Full Visibility: Huntress Managed EDR provides comprehensive visibility, detection, and response for endpoints, ensuring no threat goes unnoticed.
Ease of Use: Users appreciate its intuitive interface, making it accessible even for those not deeply familiar with cybersecurity software.
24/7 Support: Supported by expert analysts in a 24/7 Security Operations Center (SOC), ensuring continuous protection and quick response to threats.
Cons:
Cost Concerns: The service can be expensive, which might be a barrier for budget-conscious small and medium-sized businesses.
False Positives: Some users report occasional false positives, which can lead to unnecessary alerts and potential disruptions.
Defender Dependence: The platform's reliance on Microsoft Defender might limit its effectiveness in environments where Defender is not the primary security tool.
3. Cylance

Cylance is an AI-driven cybersecurity solution designed to protect against advanced threats. It offers endpoint security, managed detection and response, and zero trust network access. With a focus on proactive threat prevention and low resource usage, Cylance aims to provide robust protection for businesses of all sizes.
Cylance Pricing
Cylance's pricing is not public. Contact their support for more info.
Cylance Reviews
Cylance has an overall rating of 4.3 out of 5 stars based on 57 reviews. Users appreciate its AI-driven approach and ease of use. Check out more of our reviews here!
Pros and Cons of Cylance
Pros:
AI-Driven Security: Cylance's AI-driven solutions deliver high efficacy with minimal CPU usage, even offline, ensuring robust protection without draining system resources.
Broad, Integrated Controls: The platform offers comprehensive security across network, endpoint, and cloud, effectively stopping more malware and providing a resilient defense.
Operational Excellence: Cylance prioritizes best practices, ensuring updates are thoroughly vetted to minimize the risk of large-scale outages, maintaining system stability.
Cons:
Initial Training Period: The product requires a training period to adapt to the environment, which might demand initial effort and time from the IT team.
Dependency on AI: Heavy reliance on AI could be a concern for organizations preferring more human oversight or those less trusting of automated systems.
Complexity for Small Organizations: The extensive controls might be overwhelming for smaller organizations with limited IT resources, complicating deployment and management.
4. Threatlocker

ThreatLocker is a cybersecurity solution focused on Zero Trust endpoint protection. It offers features like allowlisting, Ringfencing™, and network control to secure applications and data. With easy deployment and centralized management, ThreatLocker aims to provide robust security for businesses of all sizes.
Threatlocker Pricing
Threatlocker's pricing is not public. Contact their support for more info.
Threatlocker Reviews
ThreatLocker has an overall rating of 4.8 out of 5 stars based on 162 reviews. Users praise its strong security features and excellent support. Check out more of our reviews here!
Pros and Cons of Threatlocker
Pros:
Zero Trust Security: ThreatLocker blocks all applications and scripts except those explicitly allowed, ensuring robust endpoint protection.
Comprehensive Protection: Defends against ransomware, zero-day vulnerabilities, and other malicious software, providing a secure environment.
Unified Audit: Centralized audit logs offer a clear view of all activities, simplifying compliance and monitoring.
Cons:
Complexity: The extensive features and configurations can be overwhelming for smaller organizations or those without dedicated IT staff.
Cost: Enterprise-level security solutions like ThreatLocker can be expensive, posing a barrier for small to medium-sized businesses.
Learning Curve: Users report a steep learning curve, requiring significant time and effort to master the platform.
5. Crowdstrike

CrowdStrike is a cybersecurity solution that leverages AI to prevent breaches. It offers endpoint security, threat intelligence, and cloud security, aiming to provide comprehensive protection for businesses of all sizes. With easy deployment and robust features, CrowdStrike ensures a secure environment for modern enterprises.
Crowdstrike Pricing
Falcon Pro: $99.99/device annually
Falcon Enterprise: $184.99/device annually
Falcon Go: $59.99/device annually
Falcon Elite: Contact sales for pricing
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
CrowdStrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users praise its advanced threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
AI-native Platform: CrowdStrike leverages artificial intelligence to enhance cybersecurity, providing advanced threat detection and response capabilities.
Comprehensive Solutions: Offers endpoint security, exposure management, identity protection, and more, ensuring robust protection across various vectors.
Industry Recognition: Recognized as a leader in cybersecurity by Gartner and Forrester, validating its effectiveness and reliability.
Cons:
Complexity for Small Businesses: The platform's extensive features can be overwhelming for smaller organizations with limited IT resources.
Cost: Advanced cybersecurity solutions like CrowdStrike can be expensive, posing a barrier for budget-conscious businesses.
False Positives: Some users report occasional false positives, which can lead to unnecessary alerts and potential disruptions.
6. Vipre EDR

Vipre EDR is a cybersecurity solution designed to provide comprehensive endpoint protection. It features easy installation, ransomware prevention, AI-powered threat investigation, and mobile accessibility. Vipre aims to offer robust security for businesses of all sizes, ensuring effective threat detection and response with minimal complexity.
Vipre EDR Pricing
Vipre EDR's pricing is not public. Contact their support for more info.
Vipre EDR Reviews
Vipre EDR has an overall rating of 4.5 out of 5 stars based on 50 reviews. Users appreciate its robust threat detection and ease of use. Check out more of our reviews here!
Pros and Cons of Vipre EDR
Pros:
Easy Installation: VIPRE EDR combines advanced functionality with simple installation, making it accessible for businesses of all sizes.
Ransomware Prevention: Utilizes real-time behavior monitoring and AI to detect, prevent, and roll back ransomware attacks effectively.
Comprehensive Threat View: Provides a centralized location for viewing, investigating, and addressing threats, ensuring no threat goes unnoticed.
Cons:
Limited Reviews: There are not enough user reviews to provide comprehensive buying insights, which may deter potential customers.
Profile Limitations: The claimed profile on review sites has limited features, potentially affecting the visibility and credibility of the product.
Security Information: The seller has not added detailed security information, leaving users to request this crucial data independently.
7. Avast Endpoint Protection

Avast Endpoint Protection is a cybersecurity solution designed to safeguard businesses from cyber threats. It offers comprehensive endpoint security, easy deployment, and centralized management. With features like antivirus, firewall, and behavior analysis, Avast aims to provide robust protection for businesses of all sizes, ensuring a secure and efficient environment.
Avast Endpoint Protection Pricing
Avast Essential Business Security: $148.36/year
Avast Premium Business Security: $187.00/year
Avast Ultimate Business Security: $227.08/year
Avast Endpoint Protection Reviews
Avast Endpoint Protection has an overall rating of 4.4 out of 5 stars based on 101 reviews. Users appreciate its rich security features and user-friendly controls. Check out more of our reviews here!
Pros and Cons of Avast Endpoint Protection
Pros:
Ease of Use: Avast Endpoint Protection is user-friendly, making it accessible even for those not well-versed in cybersecurity.
Comprehensive Protection: Offers a suite of tools including antivirus, VPN, and cleanup utilities, ensuring robust security.
Global Trust: Trusted by millions worldwide, reflecting its reliability and effectiveness in protecting against threats.
Cons:
Privacy Concerns: Past issues with data privacy and selling user data have raised concerns among users.
Pop-up Ads: The free version includes pop-up ads, which can be intrusive and prompt users to upgrade.
Resource Usage: While generally lightweight, some users report performance impacts on older devices.
8. WatchGuard Panda Adaptive Defense 360

WatchGuard Panda Adaptive Defense 360 is a cybersecurity solution designed to provide advanced endpoint protection. It combines Endpoint Protection (EPP) and Endpoint Detection and Response (EDR) capabilities, offering continuous monitoring, threat hunting, and automated response. Ideal for businesses of all sizes, it ensures robust security with minimal complexity.
WatchGuard Panda Adaptive Defense 360 Pricing
WatchGuard Panda Adaptive Defense 360's pricing is not public. Contact their support for more info.
WatchGuard Panda Adaptive Defense 360 Reviews
WatchGuard Panda Adaptive Defense 360 has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its robust protection and ease of use. Check out more of our reviews here!
Pros and Cons of WatchGuard Panda Adaptive Defense 360
Pros:
Zero-Trust Application Service: Ensures 100% classification of processes, blocking any suspicious activity, enhancing overall security.
Automated Detection and Response: Reduces detection, response, and investigation time, streamlining threat management.
Forensic Information: Provides detailed forensic data to investigate attacks and mitigate effects, aiding in comprehensive threat analysis.
Cons:
Complexity: The advanced features and comprehensive protection might require significant expertise to manage effectively.
Cost: Advanced security solutions like AD360 can be expensive, which might be a consideration for smaller organizations.
Dependency on Cloud: As a cloud-delivered solution, it may require reliable internet connectivity and could be less effective in environments with limited or no internet access.
9. Carbon Black

Carbon Black is a cybersecurity solution designed to protect endpoints from advanced threats. It offers real-time threat detection, response, and prevention, ensuring robust security for businesses of all sizes. With easy deployment and AI-driven insights, Carbon Black aims to provide comprehensive protection with minimal complexity.
Carbon Black Pricing
Carbon Black's pricing is not public. Contact their support for more info.
Carbon Black Reviews
Carbon Black has an overall rating of 4.3 out of 5 stars based on 37 reviews. Users appreciate its ease of installation and robust protection. Check out more of our reviews here!
Pros and Cons of Carbon Black
Pros:
Robust Protection: Carbon Black offers strong defense against various cyber threats, ensuring comprehensive security for endpoints.
Easy Installation: Users find the installation process straightforward, making it accessible even for those with limited technical expertise.
Effective Monitoring: The platform provides excellent monitoring capabilities, allowing for real-time threat detection and response.
Cons:
Agent Removal Issues: Some users report difficulties in removing the agent, which can complicate system management.
Complex Installation: Despite its ease for some, others find the installation process complex and time-consuming.
Delay Issues: There are mentions of delays in certain functionalities, which can affect overall performance.
10. Trend Vision One

Trend Vision One is an endpoint security solution designed to defend against cyber threats at every stage of an attack. It offers centralized management, advanced threat protection, and streamlined IT operations. With features like EDR and XDR, Trend Vision One aims to provide comprehensive security for businesses of all sizes.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its unified platform and comprehensive threat intelligence. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Consolidated Security: Provides a unified view for endpoint, server, and workload security, simplifying management and enhancing visibility.
Enhanced Detection and Response: Advanced EDR and XDR capabilities ensure effective threat detection, investigation, and response.
Operational Efficiency: Centralized management streamlines IT operations, covering inventory, detections, risk mitigation, policies, and licenses.
Cons:
Complexity: The comprehensive nature of the solution might be challenging to implement and manage for smaller organizations.
Cost: Advanced features and managed services can be expensive, posing a barrier for budget-conscious businesses.
Learning Curve: Users may require training to fully utilize the platform's advanced capabilities, impacting initial deployment.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern work landscape. Try Twingate for Free today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
The Best 10 Alternatives to NinjaOne (+ Pricing & Reviews)
Twingate Team
•
Jul 27, 2024

NinjaOne provides unified IT management solutions that help IT teams manage, secure, and support endpoints. Their platform includes features like endpoint management, remote control, RMM, backup, patch management, and more. While NinjaOne offers robust solutions, it might not be the choice for everyone. This article explores the benefits and considerations of using NinjaOne.

10 Alternatives to NinjaOne
1. Symantec

Symantec is a comprehensive cybersecurity solution designed to protect large enterprises. It offers data-centric hybrid security, compliance, remote work security, and threat protection. With a focus on innovation and AI, Symantec aims to provide robust security measures that adapt to organizational changes and integrate seamlessly with existing infrastructures.
Symantec Pricing
Symantec's pricing is not public. Contact their support for more info.
Symantec Reviews
Symantec has an overall rating of 4.3 out of 5 stars based on 37 reviews. Users appreciate its advanced security features and ease of use. Check out more of our reviews here!
Pros and Cons of Symantec
Pros:
Symantec Enterprise Cloud offers comprehensive security, covering devices, private data centers, and the cloud, ensuring robust protection across all platforms.
It ensures consistent compliance, making it easier for enterprises to manage and apply compliance controls across their entire infrastructure.
With its secure remote work capabilities, Symantec protects critical enterprise assets regardless of their location, enhancing security for distributed workforces.
Cons:
The advanced features and comprehensive nature of Symantec may be too complex or costly for smaller organizations, making it more suitable for large enterprises.
While Symantec supports migration between on-premises and cloud environments, the process can still pose challenges for some organizations.
Heavy reliance on AI and automation might raise concerns about the accuracy and reliability of threat detection and response in certain scenarios.
2. Huntress Managed EDR

Huntress Managed EDR is a cybersecurity solution designed to provide full visibility, detection, and response for endpoints. It defends against attacks in real-time, ensuring comprehensive protection. With easy deployment and a user-friendly interface, it’s ideal for small and medium-sized businesses looking to enhance their security posture.
Huntress Managed EDR Pricing
Huntress Managed EDR's pricing is not public. Contact their support for more info.
Huntress Managed EDR Reviews
Huntress Managed EDR has an overall rating of 4.9 out of 5 stars based on 663 reviews. Users appreciate its ease of use and effective threat detection. Check out more of our reviews here!
Pros and Cons ofHuntress Managed EDR
Pros:
Full Visibility: Huntress Managed EDR provides comprehensive visibility, detection, and response for endpoints, ensuring no threat goes unnoticed.
Ease of Use: Users appreciate its intuitive interface, making it accessible even for those not deeply familiar with cybersecurity software.
24/7 Support: Supported by expert analysts in a 24/7 Security Operations Center (SOC), ensuring continuous protection and quick response to threats.
Cons:
Cost Concerns: The service can be expensive, which might be a barrier for budget-conscious small and medium-sized businesses.
False Positives: Some users report occasional false positives, which can lead to unnecessary alerts and potential disruptions.
Defender Dependence: The platform's reliance on Microsoft Defender might limit its effectiveness in environments where Defender is not the primary security tool.
3. Cylance

Cylance is an AI-driven cybersecurity solution designed to protect against advanced threats. It offers endpoint security, managed detection and response, and zero trust network access. With a focus on proactive threat prevention and low resource usage, Cylance aims to provide robust protection for businesses of all sizes.
Cylance Pricing
Cylance's pricing is not public. Contact their support for more info.
Cylance Reviews
Cylance has an overall rating of 4.3 out of 5 stars based on 57 reviews. Users appreciate its AI-driven approach and ease of use. Check out more of our reviews here!
Pros and Cons of Cylance
Pros:
AI-Driven Security: Cylance's AI-driven solutions deliver high efficacy with minimal CPU usage, even offline, ensuring robust protection without draining system resources.
Broad, Integrated Controls: The platform offers comprehensive security across network, endpoint, and cloud, effectively stopping more malware and providing a resilient defense.
Operational Excellence: Cylance prioritizes best practices, ensuring updates are thoroughly vetted to minimize the risk of large-scale outages, maintaining system stability.
Cons:
Initial Training Period: The product requires a training period to adapt to the environment, which might demand initial effort and time from the IT team.
Dependency on AI: Heavy reliance on AI could be a concern for organizations preferring more human oversight or those less trusting of automated systems.
Complexity for Small Organizations: The extensive controls might be overwhelming for smaller organizations with limited IT resources, complicating deployment and management.
4. Threatlocker

ThreatLocker is a cybersecurity solution focused on Zero Trust endpoint protection. It offers features like allowlisting, Ringfencing™, and network control to secure applications and data. With easy deployment and centralized management, ThreatLocker aims to provide robust security for businesses of all sizes.
Threatlocker Pricing
Threatlocker's pricing is not public. Contact their support for more info.
Threatlocker Reviews
ThreatLocker has an overall rating of 4.8 out of 5 stars based on 162 reviews. Users praise its strong security features and excellent support. Check out more of our reviews here!
Pros and Cons of Threatlocker
Pros:
Zero Trust Security: ThreatLocker blocks all applications and scripts except those explicitly allowed, ensuring robust endpoint protection.
Comprehensive Protection: Defends against ransomware, zero-day vulnerabilities, and other malicious software, providing a secure environment.
Unified Audit: Centralized audit logs offer a clear view of all activities, simplifying compliance and monitoring.
Cons:
Complexity: The extensive features and configurations can be overwhelming for smaller organizations or those without dedicated IT staff.
Cost: Enterprise-level security solutions like ThreatLocker can be expensive, posing a barrier for small to medium-sized businesses.
Learning Curve: Users report a steep learning curve, requiring significant time and effort to master the platform.
5. Crowdstrike

CrowdStrike is a cybersecurity solution that leverages AI to prevent breaches. It offers endpoint security, threat intelligence, and cloud security, aiming to provide comprehensive protection for businesses of all sizes. With easy deployment and robust features, CrowdStrike ensures a secure environment for modern enterprises.
Crowdstrike Pricing
Falcon Pro: $99.99/device annually
Falcon Enterprise: $184.99/device annually
Falcon Go: $59.99/device annually
Falcon Elite: Contact sales for pricing
Falcon Complete MDR: Contact sales for pricing
Crowdstrike Reviews
CrowdStrike has an overall rating of 4.7 out of 5 stars based on 278 reviews. Users praise its advanced threat intelligence and ease of use. Check out more of our reviews here!
Pros and Cons of Crowdstrike
Pros:
AI-native Platform: CrowdStrike leverages artificial intelligence to enhance cybersecurity, providing advanced threat detection and response capabilities.
Comprehensive Solutions: Offers endpoint security, exposure management, identity protection, and more, ensuring robust protection across various vectors.
Industry Recognition: Recognized as a leader in cybersecurity by Gartner and Forrester, validating its effectiveness and reliability.
Cons:
Complexity for Small Businesses: The platform's extensive features can be overwhelming for smaller organizations with limited IT resources.
Cost: Advanced cybersecurity solutions like CrowdStrike can be expensive, posing a barrier for budget-conscious businesses.
False Positives: Some users report occasional false positives, which can lead to unnecessary alerts and potential disruptions.
6. Vipre EDR

Vipre EDR is a cybersecurity solution designed to provide comprehensive endpoint protection. It features easy installation, ransomware prevention, AI-powered threat investigation, and mobile accessibility. Vipre aims to offer robust security for businesses of all sizes, ensuring effective threat detection and response with minimal complexity.
Vipre EDR Pricing
Vipre EDR's pricing is not public. Contact their support for more info.
Vipre EDR Reviews
Vipre EDR has an overall rating of 4.5 out of 5 stars based on 50 reviews. Users appreciate its robust threat detection and ease of use. Check out more of our reviews here!
Pros and Cons of Vipre EDR
Pros:
Easy Installation: VIPRE EDR combines advanced functionality with simple installation, making it accessible for businesses of all sizes.
Ransomware Prevention: Utilizes real-time behavior monitoring and AI to detect, prevent, and roll back ransomware attacks effectively.
Comprehensive Threat View: Provides a centralized location for viewing, investigating, and addressing threats, ensuring no threat goes unnoticed.
Cons:
Limited Reviews: There are not enough user reviews to provide comprehensive buying insights, which may deter potential customers.
Profile Limitations: The claimed profile on review sites has limited features, potentially affecting the visibility and credibility of the product.
Security Information: The seller has not added detailed security information, leaving users to request this crucial data independently.
7. Avast Endpoint Protection

Avast Endpoint Protection is a cybersecurity solution designed to safeguard businesses from cyber threats. It offers comprehensive endpoint security, easy deployment, and centralized management. With features like antivirus, firewall, and behavior analysis, Avast aims to provide robust protection for businesses of all sizes, ensuring a secure and efficient environment.
Avast Endpoint Protection Pricing
Avast Essential Business Security: $148.36/year
Avast Premium Business Security: $187.00/year
Avast Ultimate Business Security: $227.08/year
Avast Endpoint Protection Reviews
Avast Endpoint Protection has an overall rating of 4.4 out of 5 stars based on 101 reviews. Users appreciate its rich security features and user-friendly controls. Check out more of our reviews here!
Pros and Cons of Avast Endpoint Protection
Pros:
Ease of Use: Avast Endpoint Protection is user-friendly, making it accessible even for those not well-versed in cybersecurity.
Comprehensive Protection: Offers a suite of tools including antivirus, VPN, and cleanup utilities, ensuring robust security.
Global Trust: Trusted by millions worldwide, reflecting its reliability and effectiveness in protecting against threats.
Cons:
Privacy Concerns: Past issues with data privacy and selling user data have raised concerns among users.
Pop-up Ads: The free version includes pop-up ads, which can be intrusive and prompt users to upgrade.
Resource Usage: While generally lightweight, some users report performance impacts on older devices.
8. WatchGuard Panda Adaptive Defense 360

WatchGuard Panda Adaptive Defense 360 is a cybersecurity solution designed to provide advanced endpoint protection. It combines Endpoint Protection (EPP) and Endpoint Detection and Response (EDR) capabilities, offering continuous monitoring, threat hunting, and automated response. Ideal for businesses of all sizes, it ensures robust security with minimal complexity.
WatchGuard Panda Adaptive Defense 360 Pricing
WatchGuard Panda Adaptive Defense 360's pricing is not public. Contact their support for more info.
WatchGuard Panda Adaptive Defense 360 Reviews
WatchGuard Panda Adaptive Defense 360 has an overall rating of 4.4 out of 5 stars based on 115 reviews. Users appreciate its robust protection and ease of use. Check out more of our reviews here!
Pros and Cons of WatchGuard Panda Adaptive Defense 360
Pros:
Zero-Trust Application Service: Ensures 100% classification of processes, blocking any suspicious activity, enhancing overall security.
Automated Detection and Response: Reduces detection, response, and investigation time, streamlining threat management.
Forensic Information: Provides detailed forensic data to investigate attacks and mitigate effects, aiding in comprehensive threat analysis.
Cons:
Complexity: The advanced features and comprehensive protection might require significant expertise to manage effectively.
Cost: Advanced security solutions like AD360 can be expensive, which might be a consideration for smaller organizations.
Dependency on Cloud: As a cloud-delivered solution, it may require reliable internet connectivity and could be less effective in environments with limited or no internet access.
9. Carbon Black

Carbon Black is a cybersecurity solution designed to protect endpoints from advanced threats. It offers real-time threat detection, response, and prevention, ensuring robust security for businesses of all sizes. With easy deployment and AI-driven insights, Carbon Black aims to provide comprehensive protection with minimal complexity.
Carbon Black Pricing
Carbon Black's pricing is not public. Contact their support for more info.
Carbon Black Reviews
Carbon Black has an overall rating of 4.3 out of 5 stars based on 37 reviews. Users appreciate its ease of installation and robust protection. Check out more of our reviews here!
Pros and Cons of Carbon Black
Pros:
Robust Protection: Carbon Black offers strong defense against various cyber threats, ensuring comprehensive security for endpoints.
Easy Installation: Users find the installation process straightforward, making it accessible even for those with limited technical expertise.
Effective Monitoring: The platform provides excellent monitoring capabilities, allowing for real-time threat detection and response.
Cons:
Agent Removal Issues: Some users report difficulties in removing the agent, which can complicate system management.
Complex Installation: Despite its ease for some, others find the installation process complex and time-consuming.
Delay Issues: There are mentions of delays in certain functionalities, which can affect overall performance.
10. Trend Vision One

Trend Vision One is an endpoint security solution designed to defend against cyber threats at every stage of an attack. It offers centralized management, advanced threat protection, and streamlined IT operations. With features like EDR and XDR, Trend Vision One aims to provide comprehensive security for businesses of all sizes.
Trend Vision One Pricing
Trend Vision One's pricing is not public. Contact their support for more info.
Trend Vision One Reviews
Trend Vision One has an overall rating of 4.7 out of 5 stars based on 183 reviews. Users appreciate its unified platform and comprehensive threat intelligence. Check out more of our reviews here!
Pros and Cons of Trend Vision One
Pros:
Consolidated Security: Provides a unified view for endpoint, server, and workload security, simplifying management and enhancing visibility.
Enhanced Detection and Response: Advanced EDR and XDR capabilities ensure effective threat detection, investigation, and response.
Operational Efficiency: Centralized management streamlines IT operations, covering inventory, detections, risk mitigation, policies, and licenses.
Cons:
Complexity: The comprehensive nature of the solution might be challenging to implement and manage for smaller organizations.
Cost: Advanced features and managed services can be expensive, posing a barrier for budget-conscious businesses.
Learning Curve: Users may require training to fully utilize the platform's advanced capabilities, impacting initial deployment.
Looking to secure your technical infrastructure?
Twingate offers granular access controls and deployment automations to protect your VPC environment. By leveraging Zero Trust security tools, Twingate ensures that private resources and internet traffic remain secure in the modern work landscape. Try Twingate for Free today!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions