Visualize and Analyze Network Log Data with Twingate and Datadog
Emily Lehman
•
Jan 24, 2023

Today we’re excited to announce the new Twingate and Datadog integration! Datadog is a modern monitoring and security platform that makes your applications, infrastructure, and third-party services observable, enabling businesses to secure their systems, avoid downtime, and ensure the best possible end-user experience. Customers can now conveniently visualize and analyze real-time data from Twingate Connectors directly within the Datadog platform.
As businesses face more frequent cyberattacks across an increasingly distributed workforce, it’s critical for organizations to close off exposed entry points without sacrificing usability or speed. Twingate’s Zero Trust alternative to VPNs enables teams to easily implement least privilege access with no impact on user performance or latency. Twingate Connectors sit behind your firewall, within the private network that protected resources are connected to, organizations using this new integration gain critical insights into resource usage and access without exposing themselves to the public internet.
With the new Twingate and Datadog integration, users can easily configure their Twingate Connectors to send real-time network logs from their Connectors to Datadog, providing an additional layer of security. Improved monitoring capability makes key Twingate metrics – including data transfer amounts, resource access activity, security policy data, and more – observable within the Datadog platform.
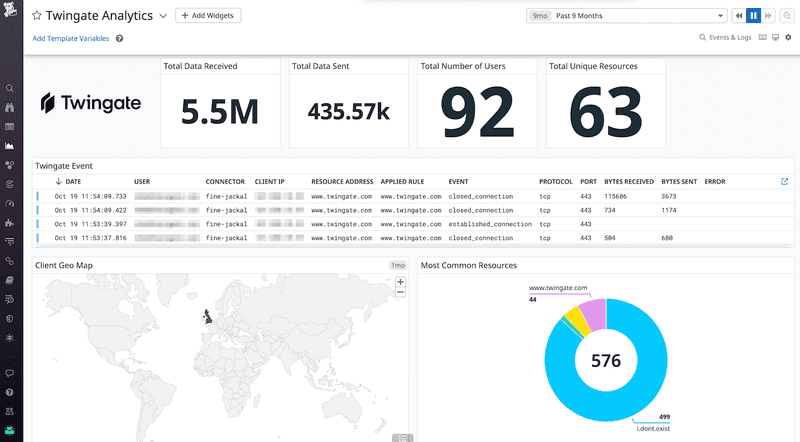
This integration provides the ability to trigger alerts in their Datadog platform based on unusual patterns in network-log data, enabling teams to quickly identify and mitigate the impact of any potential suspicious activity. Customers can also monitor end-user IP addresses, so organizations can identify connection attempts from sanctioned or high-risk countries.
Beyond just improvements in security, teams can drive efficiencies and eliminate redundancies in resource access thanks to visualized data showing which users are accessing which resources.
You can find full details on setting up your Twingate and Datadog integration here. Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Visualize and Analyze Network Log Data with Twingate and Datadog
Emily Lehman
•
Jan 24, 2023

Today we’re excited to announce the new Twingate and Datadog integration! Datadog is a modern monitoring and security platform that makes your applications, infrastructure, and third-party services observable, enabling businesses to secure their systems, avoid downtime, and ensure the best possible end-user experience. Customers can now conveniently visualize and analyze real-time data from Twingate Connectors directly within the Datadog platform.
As businesses face more frequent cyberattacks across an increasingly distributed workforce, it’s critical for organizations to close off exposed entry points without sacrificing usability or speed. Twingate’s Zero Trust alternative to VPNs enables teams to easily implement least privilege access with no impact on user performance or latency. Twingate Connectors sit behind your firewall, within the private network that protected resources are connected to, organizations using this new integration gain critical insights into resource usage and access without exposing themselves to the public internet.
With the new Twingate and Datadog integration, users can easily configure their Twingate Connectors to send real-time network logs from their Connectors to Datadog, providing an additional layer of security. Improved monitoring capability makes key Twingate metrics – including data transfer amounts, resource access activity, security policy data, and more – observable within the Datadog platform.

This integration provides the ability to trigger alerts in their Datadog platform based on unusual patterns in network-log data, enabling teams to quickly identify and mitigate the impact of any potential suspicious activity. Customers can also monitor end-user IP addresses, so organizations can identify connection attempts from sanctioned or high-risk countries.
Beyond just improvements in security, teams can drive efficiencies and eliminate redundancies in resource access thanks to visualized data showing which users are accessing which resources.
You can find full details on setting up your Twingate and Datadog integration here. Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Visualize and Analyze Network Log Data with Twingate and Datadog
Emily Lehman
•
Jan 24, 2023

Today we’re excited to announce the new Twingate and Datadog integration! Datadog is a modern monitoring and security platform that makes your applications, infrastructure, and third-party services observable, enabling businesses to secure their systems, avoid downtime, and ensure the best possible end-user experience. Customers can now conveniently visualize and analyze real-time data from Twingate Connectors directly within the Datadog platform.
As businesses face more frequent cyberattacks across an increasingly distributed workforce, it’s critical for organizations to close off exposed entry points without sacrificing usability or speed. Twingate’s Zero Trust alternative to VPNs enables teams to easily implement least privilege access with no impact on user performance or latency. Twingate Connectors sit behind your firewall, within the private network that protected resources are connected to, organizations using this new integration gain critical insights into resource usage and access without exposing themselves to the public internet.
With the new Twingate and Datadog integration, users can easily configure their Twingate Connectors to send real-time network logs from their Connectors to Datadog, providing an additional layer of security. Improved monitoring capability makes key Twingate metrics – including data transfer amounts, resource access activity, security policy data, and more – observable within the Datadog platform.

This integration provides the ability to trigger alerts in their Datadog platform based on unusual patterns in network-log data, enabling teams to quickly identify and mitigate the impact of any potential suspicious activity. Customers can also monitor end-user IP addresses, so organizations can identify connection attempts from sanctioned or high-risk countries.
Beyond just improvements in security, teams can drive efficiencies and eliminate redundancies in resource access thanks to visualized data showing which users are accessing which resources.
You can find full details on setting up your Twingate and Datadog integration here. Not a Twingate customer yet? If you’re interested in taking Twingate for a spin, you can request a personalized demo from our team or try it out yourself for free.
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions