Challenges with Securing CI/CD Pipelines and How Zero Trust Can Help
Twingate Team
•
•
Sep 24, 2024

Challenges with Securing CI/CD Pipelines and How Zero Trust Can Help: A Swiss Cheese Model Approach
Building software is like playing an endless game of updates—new features, UI tweaks, database changes, and more. CI/CD pipelines automate the code build, test, and deploy process, making DevOps workflows faster and more efficient. But with that speed comes security risks. Each tool and integration can create potential entry points for threats, much like holes in Swiss cheese.
The Swiss Cheese Model: Understanding CI/CD Pipeline Vulnerabilities
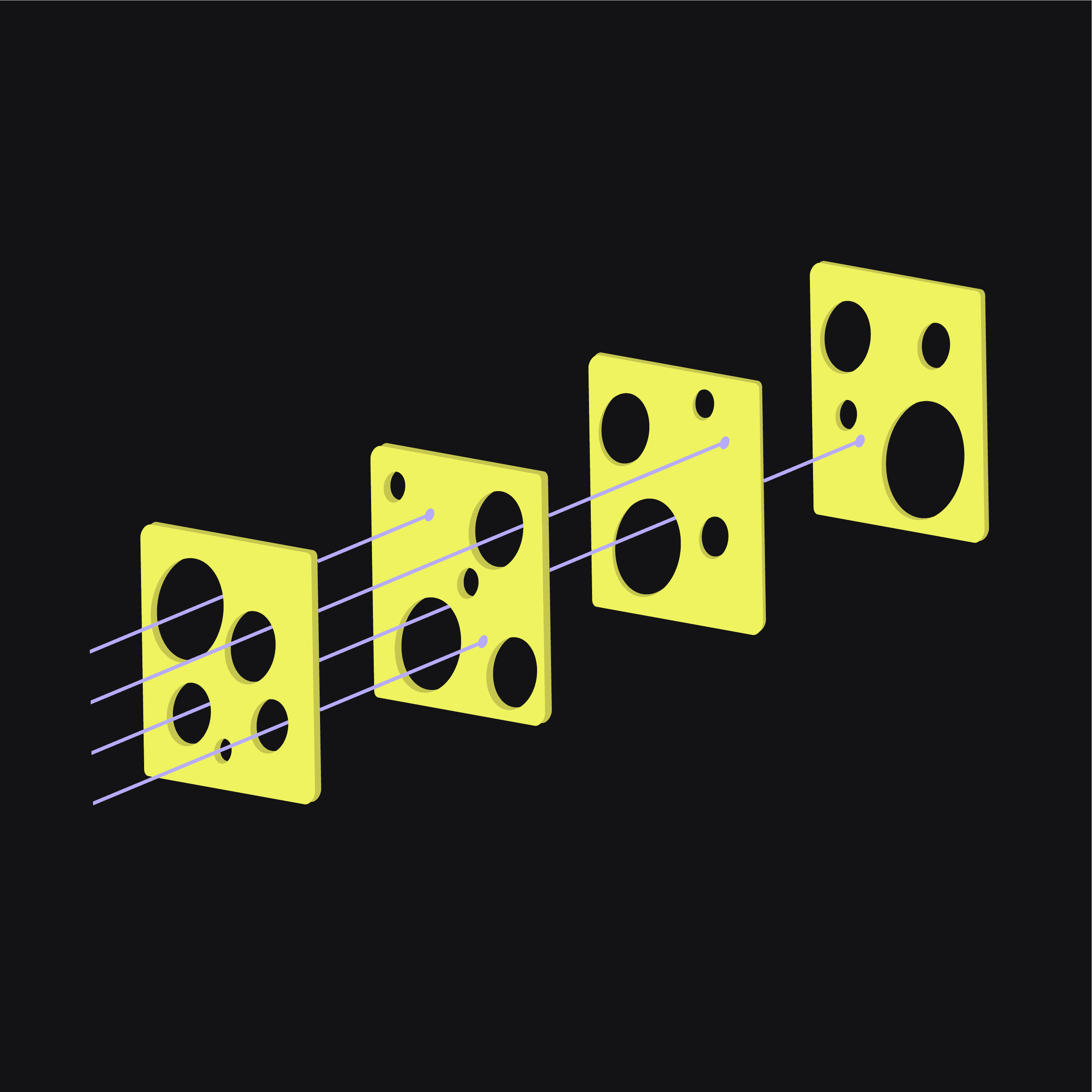
Imagine your CI/CD pipeline as layers of Swiss cheese stacked together. Each layer represents a different stage of development—coding, testing, deploying—with its own potential security gaps. If the holes align just right, a threat can pass through all layers, causing a breach.
In traditional setups, security was treated as a separate step, often after deployment, making it time-consuming and costly to fix issues. But in a secure CI/CD pipeline, security isn't an afterthought—it's integrated from the get-go, starting from planning and continuing through every phase. This is where the Swiss cheese model shines: by recognizing that each layer has weaknesses, you can strategically place defenses to minimize the chances of a security incident.
Key Steps to Building a Secure CI/CD Pipeline
1. Security Policies at Every Step: Security starts with solid policies. From development to deployment, set clear guidelines to reduce threats at every stage. Establish a standard security policy for the overall company with stricter policies for more sensitive resources.
2. Security-Driven Development: Developers often focus on shipping features quickly, but it's crucial they also code with security in mind. Guidelines and best practices from security pros can help developers identify potential issues before they even start coding.
3. Secure Testing Environments: Automated testing tools can catch vulnerabilities in front-end, back-end, databases, and APIs before they become real problems. Think of it as plugging the holes before they become a path through the cheese.
4. Code Review Processes: Peer reviews aren't just for catching bugs—they're also an opportunity to instill a security mindset. Seasoned devs can train the newer ones, ensuring security is baked in, not bolted on.
5. Tighten Access Controls: Not everyone needs access to everything. Define who can access what in your CI/CD pipeline, regularly audit permissions, and rotate passwords to keep things locked down.
6. Safeguard Secrets: API tokens, encryption keys, and credentials need their own vaults with strict controls. Regular audits help keep your secrets... well, secret.
7. Automate with Infrastructure as Code (IaC): Tools like Terraform and Ansible automate environment setup, reducing the chance of human error and providing a consistent, secure infrastructure for your CI/CD pipeline.
8. Ready Rollbacks: No matter how much effort you put into securing your pipeline, vulnerabilities can still sneak in. Always keep backups of stable builds so you can quickly roll back if something goes wrong.
9. Cultural Shift Towards Security: Security isn’t just a checkbox; it’s a mindset. Encourage a culture where everyone, from developers to testers, thinks about security at every stage. This shift is crucial as cyber-attacks become more frequent and sophisticated.
The Zero Trust Approach: Layered Security for CI/CD Pipelines
The Zero Trust model takes the Swiss cheese analogy a step further by assuming every layer is compromised. Instead of trusting any layer by default, Zero Trust requires continuous verification of every interaction within your CI/CD pipeline. This approach ensures that even if one layer has a gap, it won’t be a straight path for threats.
How Zero Trust Can Help:
Granular Access Controls: Only allow access to those who need it—and only to the parts they need.
Least Privilege: Each process, service, and user gets the minimum permissions required, reducing the attack surface.
Continuous Monitoring: Constantly watch for anomalies and threats, ensuring no layer is left unguarded.
Final Thoughts
Securing CI/CD pipelines isn't just about fixing a few bugs or adding extra layers; it's about strategically aligning those layers to minimize risks. By integrating Zero Trust principles and treating every layer as a potential vulnerability, you can build a more secure pipeline that keeps threats out. The goal is to make sure that the "holes" in your Swiss cheese never line up, blocking attacks at every step of the way.
Twingate’s Zero Trust Network Access (ZTNA) solution provides a seamless way for DevOps to secure CI/CD pipelines by enforcing granular access controls based on least-privilege principles. With Twingate, you can lock down access to critical resources without re-architecting your existing network, ensuring that only the right people and processes have access to the right parts of your pipeline. Whether your resources are in the cloud or on-premises, Twingate’s ZTNA helps keep your CI/CD pipeline secure, compliant, and resilient against threats. Try Twingate’s free Starter plan to experience how easy it is to protect your CI/CD pipeline with Zero Trust.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Challenges with Securing CI/CD Pipelines and How Zero Trust Can Help
Twingate Team
•
•
Sep 24, 2024

Challenges with Securing CI/CD Pipelines and How Zero Trust Can Help: A Swiss Cheese Model Approach
Building software is like playing an endless game of updates—new features, UI tweaks, database changes, and more. CI/CD pipelines automate the code build, test, and deploy process, making DevOps workflows faster and more efficient. But with that speed comes security risks. Each tool and integration can create potential entry points for threats, much like holes in Swiss cheese.
The Swiss Cheese Model: Understanding CI/CD Pipeline Vulnerabilities
Imagine your CI/CD pipeline as layers of Swiss cheese stacked together. Each layer represents a different stage of development—coding, testing, deploying—with its own potential security gaps. If the holes align just right, a threat can pass through all layers, causing a breach.
In traditional setups, security was treated as a separate step, often after deployment, making it time-consuming and costly to fix issues. But in a secure CI/CD pipeline, security isn't an afterthought—it's integrated from the get-go, starting from planning and continuing through every phase. This is where the Swiss cheese model shines: by recognizing that each layer has weaknesses, you can strategically place defenses to minimize the chances of a security incident.

Key Steps to Building a Secure CI/CD Pipeline
1. Security Policies at Every Step: Security starts with solid policies. From development to deployment, set clear guidelines to reduce threats at every stage. Establish a standard security policy for the overall company with stricter policies for more sensitive resources.
2. Security-Driven Development: Developers often focus on shipping features quickly, but it's crucial they also code with security in mind. Guidelines and best practices from security pros can help developers identify potential issues before they even start coding.
3. Secure Testing Environments: Automated testing tools can catch vulnerabilities in front-end, back-end, databases, and APIs before they become real problems. Think of it as plugging the holes before they become a path through the cheese.
4. Code Review Processes: Peer reviews aren't just for catching bugs—they're also an opportunity to instill a security mindset. Seasoned devs can train the newer ones, ensuring security is baked in, not bolted on.
5. Tighten Access Controls: Not everyone needs access to everything. Define who can access what in your CI/CD pipeline, regularly audit permissions, and rotate passwords to keep things locked down.
6. Safeguard Secrets: API tokens, encryption keys, and credentials need their own vaults with strict controls. Regular audits help keep your secrets... well, secret.
7. Automate with Infrastructure as Code (IaC): Tools like Terraform and Ansible automate environment setup, reducing the chance of human error and providing a consistent, secure infrastructure for your CI/CD pipeline.
8. Ready Rollbacks: No matter how much effort you put into securing your pipeline, vulnerabilities can still sneak in. Always keep backups of stable builds so you can quickly roll back if something goes wrong.
9. Cultural Shift Towards Security: Security isn’t just a checkbox; it’s a mindset. Encourage a culture where everyone, from developers to testers, thinks about security at every stage. This shift is crucial as cyber-attacks become more frequent and sophisticated.
The Zero Trust Approach: Layered Security for CI/CD Pipelines
The Zero Trust model takes the Swiss cheese analogy a step further by assuming every layer is compromised. Instead of trusting any layer by default, Zero Trust requires continuous verification of every interaction within your CI/CD pipeline. This approach ensures that even if one layer has a gap, it won’t be a straight path for threats.
How Zero Trust Can Help:
Granular Access Controls: Only allow access to those who need it—and only to the parts they need.
Least Privilege: Each process, service, and user gets the minimum permissions required, reducing the attack surface.
Continuous Monitoring: Constantly watch for anomalies and threats, ensuring no layer is left unguarded.
Final Thoughts
Securing CI/CD pipelines isn't just about fixing a few bugs or adding extra layers; it's about strategically aligning those layers to minimize risks. By integrating Zero Trust principles and treating every layer as a potential vulnerability, you can build a more secure pipeline that keeps threats out. The goal is to make sure that the "holes" in your Swiss cheese never line up, blocking attacks at every step of the way.
Twingate’s Zero Trust Network Access (ZTNA) solution provides a seamless way for DevOps to secure CI/CD pipelines by enforcing granular access controls based on least-privilege principles. With Twingate, you can lock down access to critical resources without re-architecting your existing network, ensuring that only the right people and processes have access to the right parts of your pipeline. Whether your resources are in the cloud or on-premises, Twingate’s ZTNA helps keep your CI/CD pipeline secure, compliant, and resilient against threats. Try Twingate’s free Starter plan to experience how easy it is to protect your CI/CD pipeline with Zero Trust.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Challenges with Securing CI/CD Pipelines and How Zero Trust Can Help
Twingate Team
•
•
Sep 24, 2024

Challenges with Securing CI/CD Pipelines and How Zero Trust Can Help: A Swiss Cheese Model Approach
Building software is like playing an endless game of updates—new features, UI tweaks, database changes, and more. CI/CD pipelines automate the code build, test, and deploy process, making DevOps workflows faster and more efficient. But with that speed comes security risks. Each tool and integration can create potential entry points for threats, much like holes in Swiss cheese.
The Swiss Cheese Model: Understanding CI/CD Pipeline Vulnerabilities
Imagine your CI/CD pipeline as layers of Swiss cheese stacked together. Each layer represents a different stage of development—coding, testing, deploying—with its own potential security gaps. If the holes align just right, a threat can pass through all layers, causing a breach.
In traditional setups, security was treated as a separate step, often after deployment, making it time-consuming and costly to fix issues. But in a secure CI/CD pipeline, security isn't an afterthought—it's integrated from the get-go, starting from planning and continuing through every phase. This is where the Swiss cheese model shines: by recognizing that each layer has weaknesses, you can strategically place defenses to minimize the chances of a security incident.

Key Steps to Building a Secure CI/CD Pipeline
1. Security Policies at Every Step: Security starts with solid policies. From development to deployment, set clear guidelines to reduce threats at every stage. Establish a standard security policy for the overall company with stricter policies for more sensitive resources.
2. Security-Driven Development: Developers often focus on shipping features quickly, but it's crucial they also code with security in mind. Guidelines and best practices from security pros can help developers identify potential issues before they even start coding.
3. Secure Testing Environments: Automated testing tools can catch vulnerabilities in front-end, back-end, databases, and APIs before they become real problems. Think of it as plugging the holes before they become a path through the cheese.
4. Code Review Processes: Peer reviews aren't just for catching bugs—they're also an opportunity to instill a security mindset. Seasoned devs can train the newer ones, ensuring security is baked in, not bolted on.
5. Tighten Access Controls: Not everyone needs access to everything. Define who can access what in your CI/CD pipeline, regularly audit permissions, and rotate passwords to keep things locked down.
6. Safeguard Secrets: API tokens, encryption keys, and credentials need their own vaults with strict controls. Regular audits help keep your secrets... well, secret.
7. Automate with Infrastructure as Code (IaC): Tools like Terraform and Ansible automate environment setup, reducing the chance of human error and providing a consistent, secure infrastructure for your CI/CD pipeline.
8. Ready Rollbacks: No matter how much effort you put into securing your pipeline, vulnerabilities can still sneak in. Always keep backups of stable builds so you can quickly roll back if something goes wrong.
9. Cultural Shift Towards Security: Security isn’t just a checkbox; it’s a mindset. Encourage a culture where everyone, from developers to testers, thinks about security at every stage. This shift is crucial as cyber-attacks become more frequent and sophisticated.
The Zero Trust Approach: Layered Security for CI/CD Pipelines
The Zero Trust model takes the Swiss cheese analogy a step further by assuming every layer is compromised. Instead of trusting any layer by default, Zero Trust requires continuous verification of every interaction within your CI/CD pipeline. This approach ensures that even if one layer has a gap, it won’t be a straight path for threats.
How Zero Trust Can Help:
Granular Access Controls: Only allow access to those who need it—and only to the parts they need.
Least Privilege: Each process, service, and user gets the minimum permissions required, reducing the attack surface.
Continuous Monitoring: Constantly watch for anomalies and threats, ensuring no layer is left unguarded.
Final Thoughts
Securing CI/CD pipelines isn't just about fixing a few bugs or adding extra layers; it's about strategically aligning those layers to minimize risks. By integrating Zero Trust principles and treating every layer as a potential vulnerability, you can build a more secure pipeline that keeps threats out. The goal is to make sure that the "holes" in your Swiss cheese never line up, blocking attacks at every step of the way.
Twingate’s Zero Trust Network Access (ZTNA) solution provides a seamless way for DevOps to secure CI/CD pipelines by enforcing granular access controls based on least-privilege principles. With Twingate, you can lock down access to critical resources without re-architecting your existing network, ensuring that only the right people and processes have access to the right parts of your pipeline. Whether your resources are in the cloud or on-premises, Twingate’s ZTNA helps keep your CI/CD pipeline secure, compliant, and resilient against threats. Try Twingate’s free Starter plan to experience how easy it is to protect your CI/CD pipeline with Zero Trust.
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions