How-To Guide: Use Twingate to Provide Limited Access to Contractors and Third Parties
Stuart Loh
•
Mar 2, 2021

When working from outside of the office, employees traditionally rely on VPNs to access private applications and servers on their organization’s corporate network. However, third parties like consultants, contractors, and other vendors often need temporary access to those resources as well. For example, an auditing firm may need access to on-premises financial systems for a few months, or a QA contractor may need access to a development environment for the duration of a project.
Unfortunately, provisioning access for third parties is typically a cumbersome process that is difficult to maintain and poses security risks. Read on to find out why, and learn how Twingate can help.
Firstly, setting up a user with VPN is often a lengthy, multi-step process requiring the assistance of IT support. This can be complicated when third parties bring their own equipment that is neither standard nor controlled by a company’s IT team, requiring one-off setup procedures to be developed. That equipment may also not meet the company’s security standards, meaning that it becomes a vector for threats once it obtains access to a company network.
Secondly, a new VPN account has to be provisioned for that user, and that means someone needs to remember to deprovision it when the user no longer needs access (along with any application-specific accounts that were created for the user). When there are many third parties, keeping track of who is meant to have access to what, and for how long, becomes a challenge and a security risk when things inevitably slip through the cracks.
Thirdly, VPNs grant users with access to entire networks, which may be more access than a user actually requires. This is inconsistent with the principle of least privileged access and is a less secure approach.
How Twingate Makes Controlling Access for Contractors Better
In contrast, providing limited access to third parties with Twingate is quicker, easier to keep track of, and more secure:
User setup involves simply installing an app from the Twingate website or an app store, with no configuration necessary.
On the administrative side, provisioning a user account is as simple as sending an invitation to a third party user’s email address. The user can then use a social SSO provider like G Suite to sign into Twingate.
Because Twingate controls access at a granular resource level, very specific access to applications can be granted, so that third parties have access to the minimum number of private resources necessary to do their job. Users don’t receive direct access to entire networks.
Twingate provides one central place for admins to review access controls across the enterprise, making it easy to perform periodic audits of access lists and policies. Also, deprovisioning an account in Twingate disables access to everything, even if you forget to deprovision any app-specific accounts.
Because Twingate controls access at the network layer, it is possible to protect all resources with multi-factor authentication - even for applications that don’t natively support it.
Two Step Guide to Providing Access to a Contractor
In this guide, we show how easy it is to use Twingate to give a third party access to a private resource, and nothing more. For the purposes of this guide, we will use the hypothetical example of a company called Autoco that has hired a marketing consulting firm. The firm has an analyst who provides their services remotely and needs access to an on-premises installation of Tableau, which is a visual analytics tool.
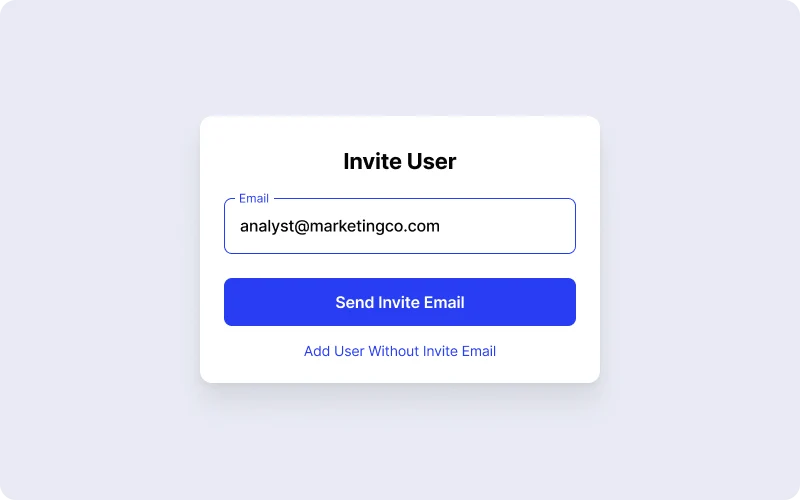
1. Add the Contractor to Twingate. Sign into your Twingate account and go to the Users page. Click +Add and provide the email address of the contractor. The contractor will receive an email with instructions on how to register for a Twingate account. They can then download, install and sign in to the Twingate client app. However, the contractor will not be able to access anything until you give them the permissions in the next step.
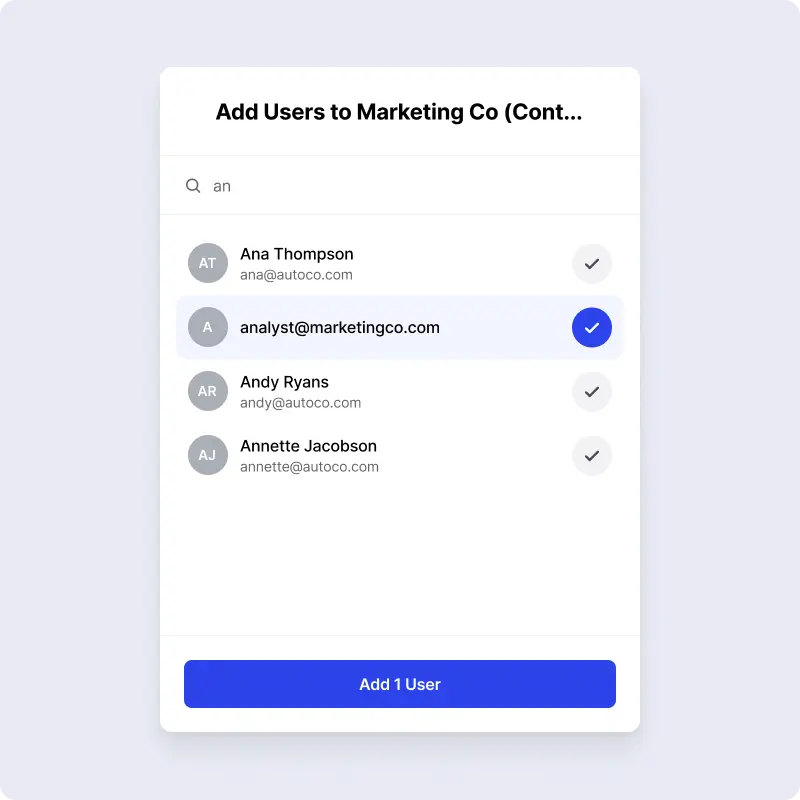
2. Create a New Group for the Contractor. Access to private resources is granted to specific Groups, and Groups are made up of Users. Because in our example Autoco doesn’t already have a Group which has access only to Tableau, we need to create a new Group. Go to the Groups page and click +Add. Name the Group, select “Social‚ as the access policy, add the User you created in Step 1, and finally add the resource they need access to. In our example, you would use the following details, and then click Done:
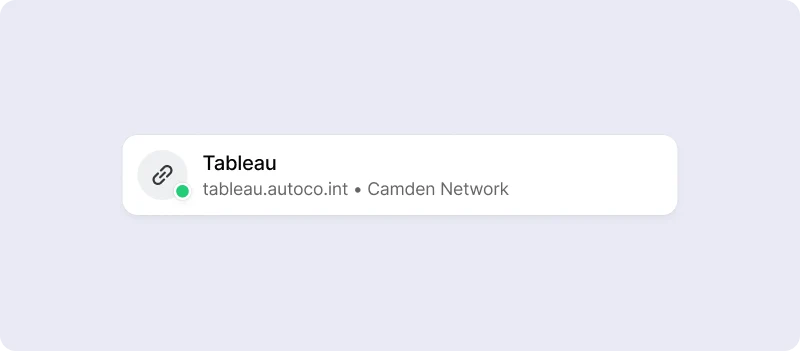
3. You’re done! It’s literally that simple. When the contractor signs into the Twingate client app, they will automatically have access to Tableau at `tableau.autoco.int`.
When the marketing firm’s project ends, you can either delete the Group and User or, if the firm may come back for a future project, simply change the Group’s status to “Disabled‚ and the contractor will automatically lose access until you’re ready to enable them again.
Try It For Yourself
If you’ve ever faced the burden of provisioning access for third parties and keeping track of who’s who, see how Twingate can make your life easier. Sign up for a free trial today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
How-To Guide: Use Twingate to Provide Limited Access to Contractors and Third Parties
Stuart Loh
•
Mar 2, 2021

When working from outside of the office, employees traditionally rely on VPNs to access private applications and servers on their organization’s corporate network. However, third parties like consultants, contractors, and other vendors often need temporary access to those resources as well. For example, an auditing firm may need access to on-premises financial systems for a few months, or a QA contractor may need access to a development environment for the duration of a project.
Unfortunately, provisioning access for third parties is typically a cumbersome process that is difficult to maintain and poses security risks. Read on to find out why, and learn how Twingate can help.
Firstly, setting up a user with VPN is often a lengthy, multi-step process requiring the assistance of IT support. This can be complicated when third parties bring their own equipment that is neither standard nor controlled by a company’s IT team, requiring one-off setup procedures to be developed. That equipment may also not meet the company’s security standards, meaning that it becomes a vector for threats once it obtains access to a company network.
Secondly, a new VPN account has to be provisioned for that user, and that means someone needs to remember to deprovision it when the user no longer needs access (along with any application-specific accounts that were created for the user). When there are many third parties, keeping track of who is meant to have access to what, and for how long, becomes a challenge and a security risk when things inevitably slip through the cracks.
Thirdly, VPNs grant users with access to entire networks, which may be more access than a user actually requires. This is inconsistent with the principle of least privileged access and is a less secure approach.
How Twingate Makes Controlling Access for Contractors Better
In contrast, providing limited access to third parties with Twingate is quicker, easier to keep track of, and more secure:
User setup involves simply installing an app from the Twingate website or an app store, with no configuration necessary.
On the administrative side, provisioning a user account is as simple as sending an invitation to a third party user’s email address. The user can then use a social SSO provider like G Suite to sign into Twingate.
Because Twingate controls access at a granular resource level, very specific access to applications can be granted, so that third parties have access to the minimum number of private resources necessary to do their job. Users don’t receive direct access to entire networks.
Twingate provides one central place for admins to review access controls across the enterprise, making it easy to perform periodic audits of access lists and policies. Also, deprovisioning an account in Twingate disables access to everything, even if you forget to deprovision any app-specific accounts.
Because Twingate controls access at the network layer, it is possible to protect all resources with multi-factor authentication - even for applications that don’t natively support it.
Two Step Guide to Providing Access to a Contractor
In this guide, we show how easy it is to use Twingate to give a third party access to a private resource, and nothing more. For the purposes of this guide, we will use the hypothetical example of a company called Autoco that has hired a marketing consulting firm. The firm has an analyst who provides their services remotely and needs access to an on-premises installation of Tableau, which is a visual analytics tool.

1. Add the Contractor to Twingate. Sign into your Twingate account and go to the Users page. Click +Add and provide the email address of the contractor. The contractor will receive an email with instructions on how to register for a Twingate account. They can then download, install and sign in to the Twingate client app. However, the contractor will not be able to access anything until you give them the permissions in the next step.

2. Create a New Group for the Contractor. Access to private resources is granted to specific Groups, and Groups are made up of Users. Because in our example Autoco doesn’t already have a Group which has access only to Tableau, we need to create a new Group. Go to the Groups page and click +Add. Name the Group, select “Social‚ as the access policy, add the User you created in Step 1, and finally add the resource they need access to. In our example, you would use the following details, and then click Done:

3. You’re done! It’s literally that simple. When the contractor signs into the Twingate client app, they will automatically have access to Tableau at `tableau.autoco.int`.
When the marketing firm’s project ends, you can either delete the Group and User or, if the firm may come back for a future project, simply change the Group’s status to “Disabled‚ and the contractor will automatically lose access until you’re ready to enable them again.
Try It For Yourself
If you’ve ever faced the burden of provisioning access for third parties and keeping track of who’s who, see how Twingate can make your life easier. Sign up for a free trial today!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
How-To Guide: Use Twingate to Provide Limited Access to Contractors and Third Parties
Stuart Loh
•
Mar 2, 2021

When working from outside of the office, employees traditionally rely on VPNs to access private applications and servers on their organization’s corporate network. However, third parties like consultants, contractors, and other vendors often need temporary access to those resources as well. For example, an auditing firm may need access to on-premises financial systems for a few months, or a QA contractor may need access to a development environment for the duration of a project.
Unfortunately, provisioning access for third parties is typically a cumbersome process that is difficult to maintain and poses security risks. Read on to find out why, and learn how Twingate can help.
Firstly, setting up a user with VPN is often a lengthy, multi-step process requiring the assistance of IT support. This can be complicated when third parties bring their own equipment that is neither standard nor controlled by a company’s IT team, requiring one-off setup procedures to be developed. That equipment may also not meet the company’s security standards, meaning that it becomes a vector for threats once it obtains access to a company network.
Secondly, a new VPN account has to be provisioned for that user, and that means someone needs to remember to deprovision it when the user no longer needs access (along with any application-specific accounts that were created for the user). When there are many third parties, keeping track of who is meant to have access to what, and for how long, becomes a challenge and a security risk when things inevitably slip through the cracks.
Thirdly, VPNs grant users with access to entire networks, which may be more access than a user actually requires. This is inconsistent with the principle of least privileged access and is a less secure approach.
How Twingate Makes Controlling Access for Contractors Better
In contrast, providing limited access to third parties with Twingate is quicker, easier to keep track of, and more secure:
User setup involves simply installing an app from the Twingate website or an app store, with no configuration necessary.
On the administrative side, provisioning a user account is as simple as sending an invitation to a third party user’s email address. The user can then use a social SSO provider like G Suite to sign into Twingate.
Because Twingate controls access at a granular resource level, very specific access to applications can be granted, so that third parties have access to the minimum number of private resources necessary to do their job. Users don’t receive direct access to entire networks.
Twingate provides one central place for admins to review access controls across the enterprise, making it easy to perform periodic audits of access lists and policies. Also, deprovisioning an account in Twingate disables access to everything, even if you forget to deprovision any app-specific accounts.
Because Twingate controls access at the network layer, it is possible to protect all resources with multi-factor authentication - even for applications that don’t natively support it.
Two Step Guide to Providing Access to a Contractor
In this guide, we show how easy it is to use Twingate to give a third party access to a private resource, and nothing more. For the purposes of this guide, we will use the hypothetical example of a company called Autoco that has hired a marketing consulting firm. The firm has an analyst who provides their services remotely and needs access to an on-premises installation of Tableau, which is a visual analytics tool.

1. Add the Contractor to Twingate. Sign into your Twingate account and go to the Users page. Click +Add and provide the email address of the contractor. The contractor will receive an email with instructions on how to register for a Twingate account. They can then download, install and sign in to the Twingate client app. However, the contractor will not be able to access anything until you give them the permissions in the next step.

2. Create a New Group for the Contractor. Access to private resources is granted to specific Groups, and Groups are made up of Users. Because in our example Autoco doesn’t already have a Group which has access only to Tableau, we need to create a new Group. Go to the Groups page and click +Add. Name the Group, select “Social‚ as the access policy, add the User you created in Step 1, and finally add the resource they need access to. In our example, you would use the following details, and then click Done:

3. You’re done! It’s literally that simple. When the contractor signs into the Twingate client app, they will automatically have access to Tableau at `tableau.autoco.int`.
When the marketing firm’s project ends, you can either delete the Group and User or, if the firm may come back for a future project, simply change the Group’s status to “Disabled‚ and the contractor will automatically lose access until you’re ready to enable them again.
Try It For Yourself
If you’ve ever faced the burden of provisioning access for third parties and keeping track of who’s who, see how Twingate can make your life easier. Sign up for a free trial today!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions