What is Red Team Assessment?
Twingate Team
•
•
Mar 22, 2024

Red Team Assessment is a critical component of an organization's security strategy, simulating realistic cyberattacks to evaluate the effectiveness of its defenses. This process involves a team of security experts, known as the red team, who use the tactics and methods of real-world attackers to test and find vulnerabilities in the organization’s security infrastructure.
The goal is to challenge and breach the organization's defenses, similar to how an actual attacker would, but in a controlled and safe manner. This allows for a comprehensive analysis of potential security gaps, including technological, physical, and human vulnerabilities.
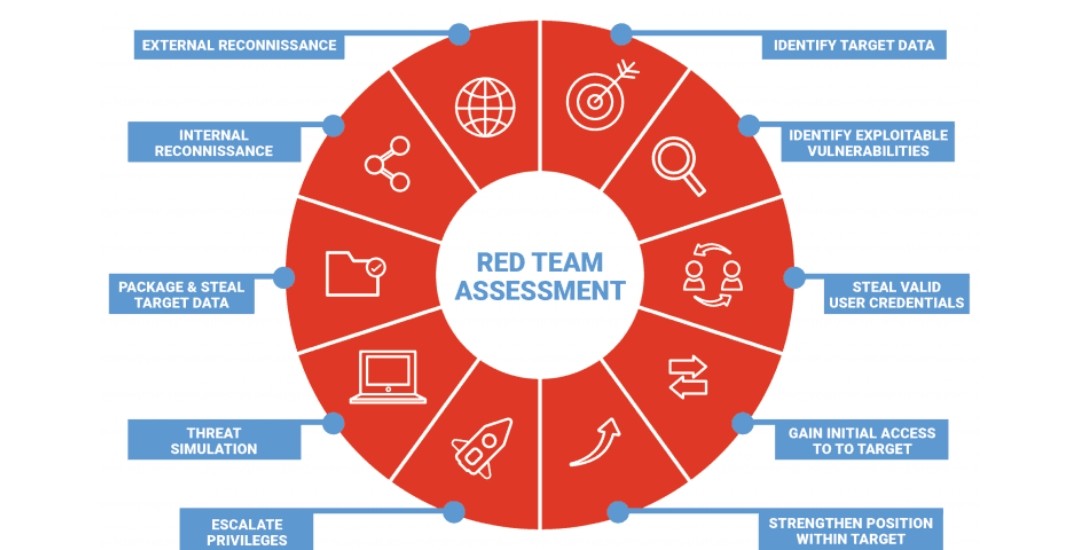
The assessment is comprehensive, covering various aspects of security from network and application vulnerabilities to social engineering and physical security. Red teaming provides a unique perspective by conducting covert operations, unlike regular security assessments where the scope and timing might be known in advance.
This method helps organizations understand how they would stand up to an unexpected, real-world attack, thereby providing insights into the effectiveness of their security posture and incident response processes.
Benefits of Red Team Assessment
Red Team Assessment offers significant advantages for enhancing organizational security:
Enhanced Security Posture: Strengthens defenses by identifying and addressing vulnerabilities before they can be exploited by real attackers.
Validation of Security Controls: Provides a real-world test of the organization's security controls and their effectiveness in preventing and responding to attacks.
Improved Incident Response: Enhances the skills and readiness of security teams by providing realistic attack scenarios for practice and evaluation.
Increased Awareness and Training: Raises security awareness across the organization and helps in training employees to recognize and respond to security threats.
Strategic Risk Management: Assists in identifying critical vulnerabilities and prioritizing security investments, leading to better risk management and resource allocation.
How Red Team Assessment Works
Red Team Assessment operates in phases, starting with planning and reconnaissance, where the team gathers information about the target, identifying potential entry points and vulnerabilities. This is followed by the attack phase, where the red team simulates various attack vectors to breach the organization's defenses.
The exercise tests not only the technological barriers but also the awareness and reaction capabilities of the organization's security personnel. After the assessment, a detailed report is provided, outlining the vulnerabilities discovered, the methods used to exploit them, and recommendations for improving the organization's security posture.
Red Team Assessment Tools & Techniques
Red Team Assessments utilize a range of tools and techniques to simulate attacks and identify vulnerabilities:
Social Engineering: Employs tactics like phishing and pretexting to test employees' susceptibility to social manipulation.
Network Penetration Testing: Utilizes tools such as Metasploit, Nmap, and Wireshark to identify and exploit vulnerabilities in network infrastructure.
Physical Security Assessments: Tests the effectiveness of physical security measures by attempting unauthorized access to facilities.
Custom Tool Development: Involves creating unique tools and scripts to simulate advanced persistent threats and bypass standard security measures.
Open Source Intelligence (OSINT): Gathers publicly available information to inform the attack strategies and identify potential entry points into the organization.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
What is Red Team Assessment?
Twingate Team
•
•
Mar 22, 2024

Red Team Assessment is a critical component of an organization's security strategy, simulating realistic cyberattacks to evaluate the effectiveness of its defenses. This process involves a team of security experts, known as the red team, who use the tactics and methods of real-world attackers to test and find vulnerabilities in the organization’s security infrastructure.
The goal is to challenge and breach the organization's defenses, similar to how an actual attacker would, but in a controlled and safe manner. This allows for a comprehensive analysis of potential security gaps, including technological, physical, and human vulnerabilities.

The assessment is comprehensive, covering various aspects of security from network and application vulnerabilities to social engineering and physical security. Red teaming provides a unique perspective by conducting covert operations, unlike regular security assessments where the scope and timing might be known in advance.
This method helps organizations understand how they would stand up to an unexpected, real-world attack, thereby providing insights into the effectiveness of their security posture and incident response processes.
Benefits of Red Team Assessment
Red Team Assessment offers significant advantages for enhancing organizational security:
Enhanced Security Posture: Strengthens defenses by identifying and addressing vulnerabilities before they can be exploited by real attackers.
Validation of Security Controls: Provides a real-world test of the organization's security controls and their effectiveness in preventing and responding to attacks.
Improved Incident Response: Enhances the skills and readiness of security teams by providing realistic attack scenarios for practice and evaluation.
Increased Awareness and Training: Raises security awareness across the organization and helps in training employees to recognize and respond to security threats.
Strategic Risk Management: Assists in identifying critical vulnerabilities and prioritizing security investments, leading to better risk management and resource allocation.
How Red Team Assessment Works
Red Team Assessment operates in phases, starting with planning and reconnaissance, where the team gathers information about the target, identifying potential entry points and vulnerabilities. This is followed by the attack phase, where the red team simulates various attack vectors to breach the organization's defenses.
The exercise tests not only the technological barriers but also the awareness and reaction capabilities of the organization's security personnel. After the assessment, a detailed report is provided, outlining the vulnerabilities discovered, the methods used to exploit them, and recommendations for improving the organization's security posture.
Red Team Assessment Tools & Techniques
Red Team Assessments utilize a range of tools and techniques to simulate attacks and identify vulnerabilities:
Social Engineering: Employs tactics like phishing and pretexting to test employees' susceptibility to social manipulation.
Network Penetration Testing: Utilizes tools such as Metasploit, Nmap, and Wireshark to identify and exploit vulnerabilities in network infrastructure.
Physical Security Assessments: Tests the effectiveness of physical security measures by attempting unauthorized access to facilities.
Custom Tool Development: Involves creating unique tools and scripts to simulate advanced persistent threats and bypass standard security measures.
Open Source Intelligence (OSINT): Gathers publicly available information to inform the attack strategies and identify potential entry points into the organization.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
What is Red Team Assessment?
Twingate Team
•
•
Mar 22, 2024

Red Team Assessment is a critical component of an organization's security strategy, simulating realistic cyberattacks to evaluate the effectiveness of its defenses. This process involves a team of security experts, known as the red team, who use the tactics and methods of real-world attackers to test and find vulnerabilities in the organization’s security infrastructure.
The goal is to challenge and breach the organization's defenses, similar to how an actual attacker would, but in a controlled and safe manner. This allows for a comprehensive analysis of potential security gaps, including technological, physical, and human vulnerabilities.

The assessment is comprehensive, covering various aspects of security from network and application vulnerabilities to social engineering and physical security. Red teaming provides a unique perspective by conducting covert operations, unlike regular security assessments where the scope and timing might be known in advance.
This method helps organizations understand how they would stand up to an unexpected, real-world attack, thereby providing insights into the effectiveness of their security posture and incident response processes.
Benefits of Red Team Assessment
Red Team Assessment offers significant advantages for enhancing organizational security:
Enhanced Security Posture: Strengthens defenses by identifying and addressing vulnerabilities before they can be exploited by real attackers.
Validation of Security Controls: Provides a real-world test of the organization's security controls and their effectiveness in preventing and responding to attacks.
Improved Incident Response: Enhances the skills and readiness of security teams by providing realistic attack scenarios for practice and evaluation.
Increased Awareness and Training: Raises security awareness across the organization and helps in training employees to recognize and respond to security threats.
Strategic Risk Management: Assists in identifying critical vulnerabilities and prioritizing security investments, leading to better risk management and resource allocation.
How Red Team Assessment Works
Red Team Assessment operates in phases, starting with planning and reconnaissance, where the team gathers information about the target, identifying potential entry points and vulnerabilities. This is followed by the attack phase, where the red team simulates various attack vectors to breach the organization's defenses.
The exercise tests not only the technological barriers but also the awareness and reaction capabilities of the organization's security personnel. After the assessment, a detailed report is provided, outlining the vulnerabilities discovered, the methods used to exploit them, and recommendations for improving the organization's security posture.
Red Team Assessment Tools & Techniques
Red Team Assessments utilize a range of tools and techniques to simulate attacks and identify vulnerabilities:
Social Engineering: Employs tactics like phishing and pretexting to test employees' susceptibility to social manipulation.
Network Penetration Testing: Utilizes tools such as Metasploit, Nmap, and Wireshark to identify and exploit vulnerabilities in network infrastructure.
Physical Security Assessments: Tests the effectiveness of physical security measures by attempting unauthorized access to facilities.
Custom Tool Development: Involves creating unique tools and scripts to simulate advanced persistent threats and bypass standard security measures.
Open Source Intelligence (OSINT): Gathers publicly available information to inform the attack strategies and identify potential entry points into the organization.
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions