New
Verify devices in Twingate using 1Password Device Trust
Website
Category
Endpoint Detection & Response Mobile Device Management
Overview
1Password, a leader in identity security, has expanded its offerings to fill critical gaps in access management and identity by enabling businesses to secure every sign-in to every application from every device. With this new integration, you can now verify devices in Twingate using 1Password Device Trust.
The integration automatically syncs device verification status every five minutes for Windows, macOS, and Linux devices. You can monitor device compliance status directly in the Twingate Admin Console.
Both Twingate and 1Password believe that security controls that are hard to use don’t get used at all. Because of that, we designed this integration to be simple and straightforward to implement:
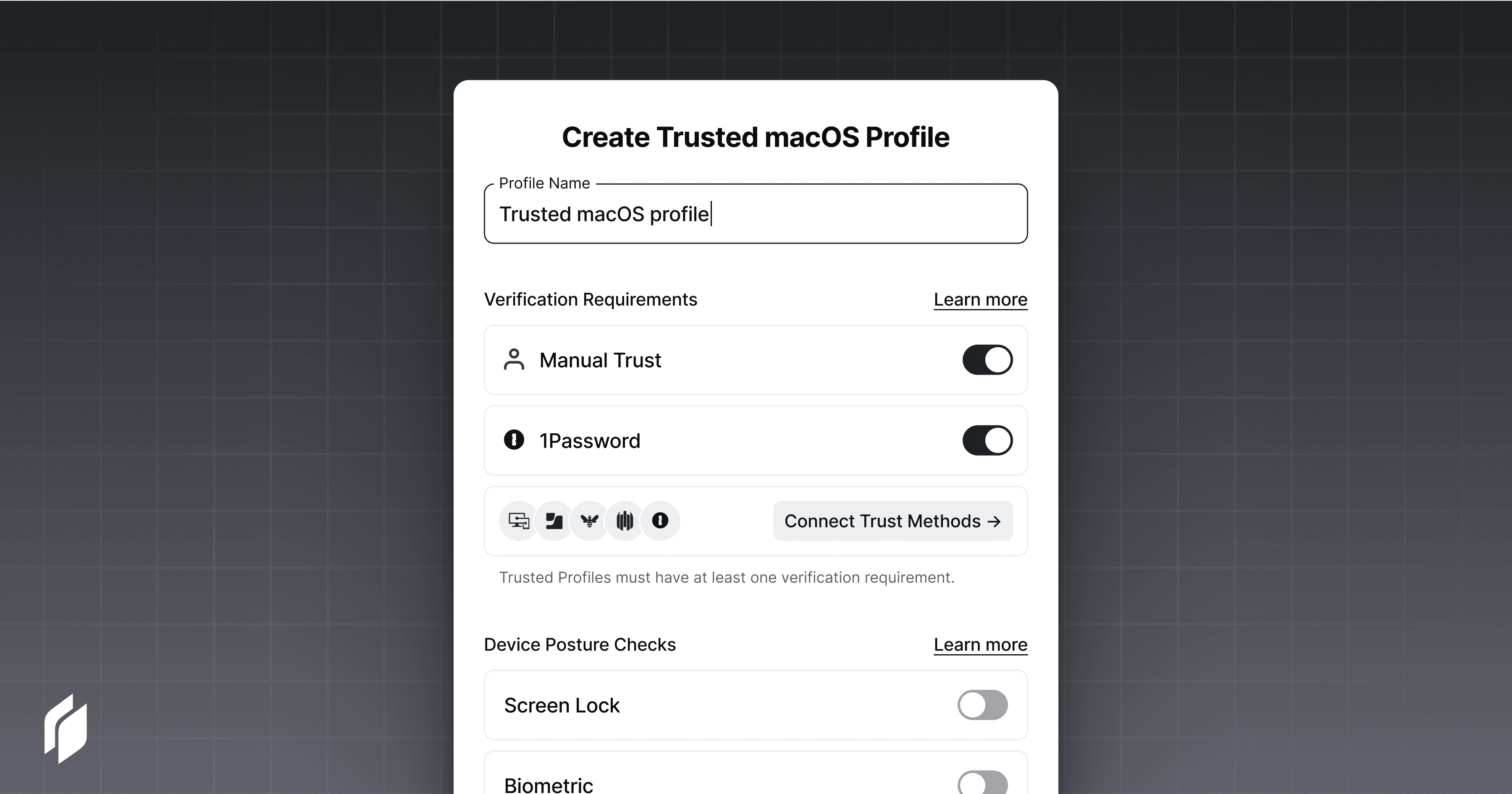
Select 1Password as a verification method for Trusted Devices under the Device Security tab of the Twingate Admin Console.
Create or edit a Trusted Profile for Windows, macOS, or Linux with 1Password enabled as a verification requirement
Apply this Trusted Profile on any Twingate protected resource where 1Password device verification is required
Benefits
Intelligent policy, at the edge
Twingate enables companies to set access policies at the endpoint device, applying the principle of least privileged access for enhanced security.
Performant protection
Unlike traditional VPNs, Twingate offers fine-grained access control and split tunneling so employee productivity is not disrupted by a slow or unreliable VPN connection.
BYOD Security
Connect 1Password's extensive library of device checks - including those for BYOD and unmanaged devices - to Twingate Security Policies.