Social Logins
Using social identities to log in to Twingate
In cases where there is no third party Identity Provider available, Twingate supports the use of social identities to log in. Administrators can invite and manage users through the Team page in the Admin Console.
Social Login Options
There are four options available:
- Microsoft
- GitHub
Users can log in with any account from one of these four providers, as long as the email address associated with the account matches the email address of the user in Twingate.
Inviting Users
In order to invite new users to your Twingate account, navigate to the users tab on the Team page in the Admin Console. Click the “Add User” button and enter their email address.
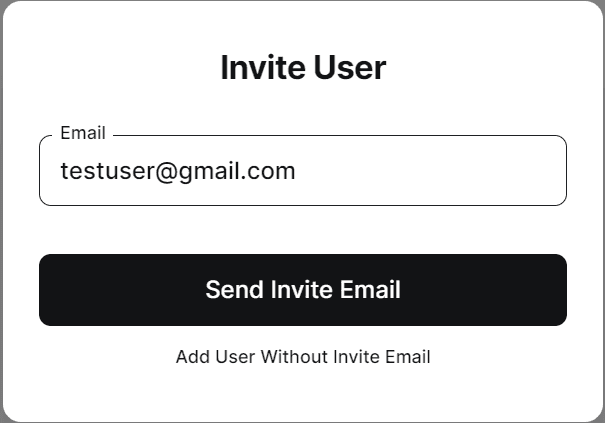
Click the “Send Invite Email” button to send the user an email with a link to download the Client and log in, or click “Add User Without Invite Email” if you don’t want them to receive an email invitation.
Managing Users
In addition to inviting new users to your Twingate account, you can also use the Teams page to manage individual users. You can assign a different Role to them (see the Admins guide for more information) as well as disable or remove them completely.

To manage an individual user, click the three dots at the right side of their record to bring up the User menu.
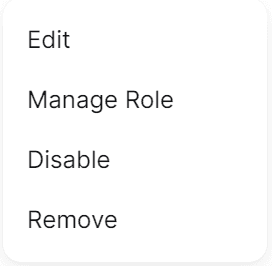
The four menu options are as follows:
Editallows you to update the user’s display nameManage Roleallows you to change the user’s role (see link above to the Admins guide)Disableallows you to temporarily disable the user without removing them, blocking their ability to log inRemoveallows you to completely delete the user
Keep in mind that disabled users are still users that will be billed for.
For more information on offboarding social users, see the Offboarding Users page.
Last updated 6 months ago